Leading Technology Companies Form Cyber Security Research Alliance
Today, leading technology companies announced the creation of the Cyber Security Research Alliance (CSRA). The CSRA is a private, non-profit research consortium formed in response to the growing need for increased public-private collaboration to address complex problems in cyber security. The founding members of the CSRI are Advanced Micro Devices (AMD), Honeywell, Intel Corporation, Lockheed Martin, and RSA/EMC.
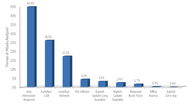
President Obama has prioritized cyber threats as one of the most serious economic and national security challenges we face as a nation and a dependency to America's economic prosperity in the 21st century.
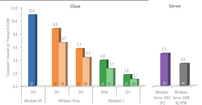
CSRA seeks to achieve coordinated industry participation to address national cyber security research and development (R&D) imperatives and bridge the gap between government funded R&D and commercially available products and solutions in cyber security. CSRA will focus on challenges that are bigger than any one company, consortium, sector or nation and ensure that government, industry and academia collaborate on in-depth problem understanding and definition.
President Obama has prioritized cyber threats as one of the most serious economic and national security challenges we face as a nation and a dependency to America's economic prosperity in the 21st century.
CSRA seeks to achieve coordinated industry participation to address national cyber security research and development (R&D) imperatives and bridge the gap between government funded R&D and commercially available products and solutions in cyber security. CSRA will focus on challenges that are bigger than any one company, consortium, sector or nation and ensure that government, industry and academia collaborate on in-depth problem understanding and definition.