qubit
Overclocked quantum bit
- Joined
- Dec 6, 2007
- Messages
- 17,865 (2.85/day)
- Location
- Quantum Well UK
| System Name | Quantumville™ |
|---|---|
| Processor | Intel Core i7-2700K @ 4GHz |
| Motherboard | Asus P8Z68-V PRO/GEN3 |
| Cooling | Noctua NH-D14 |
| Memory | 16GB (2 x 8GB Corsair Vengeance Black DDR3 PC3-12800 C9 1600MHz) |
| Video Card(s) | MSI RTX 2080 SUPER Gaming X Trio |
| Storage | Samsung 850 Pro 256GB | WD Black 4TB | WD Blue 6TB |
| Display(s) | ASUS ROG Strix XG27UQR (4K, 144Hz, G-SYNC compatible) | Asus MG28UQ (4K, 60Hz, FreeSync compatible) |
| Case | Cooler Master HAF 922 |
| Audio Device(s) | Creative Sound Blaster X-Fi Fatal1ty PCIe |
| Power Supply | Corsair AX1600i |
| Mouse | Microsoft Intellimouse Pro - Black Shadow |
| Keyboard | Yes |
| Software | Windows 10 Pro 64-bit |
Hot on the heels of our previous story of Apple Macs falling prey to a DDoS trojan, we now have another Mac trojan come on the market, as explained by Sophos. Yes, the Apple platform must indeed be becoming more popular to get this one. It's an unfortunate fact of life that the popularity of any computing platform, including smartphones, can be judged by the number of criminals who will attack it. This little nasty, called OSX/Miner-D or 'DevilRobber', hijacks Mac OS X to perform various tricks, which include minting Bitcoins (the virtual and now virtually worthless currency) stealing usernames and passwords (of course) taking screenshots and stealing the victim's Bitcoin wallet while it's at it, if there is one. And for good measure:

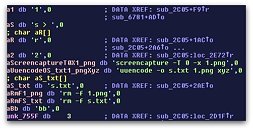
Additionally, it also looks for files matching "pthc", but it's not clear why, as Sophos reports:
This adds a really distasteful twist, doesn't it?
But how does a hapless Mac user know that their machine is infected? One of the first signs is sluggish performance and possibly extra noise from the fan on the graphics card. This is because the trojan harnesses the significant power available in today's GPU's to perform the Bitcoin mining. A mid to high end GPU can actually outperform any general purpose CPU, no matter how fast, by several orders of magnitude, which is very important when performing any cryptographic functions that require a lot of processing power, hence this particular hijack.
The trojan unsurprisingly comes as a payload within pirate software downloaded from unofficial sources. In this instance its been found in image editing application GraphicConverter v7.4, but is sure to be embedded in more dodgy software, along with improved [sic] versions of it, eventually. We wish to stress that the software house which sells GraphicConverter is innocent and is as much a victim as the unscrupulous user who downloads the hooky version.
This malware is obviously relatively sophisticated, judging by the number of nefarious functions it performs. This means that it could not have been trivial to write, test and debug, so therefore took significant time and resources of the criminals that wrote it. They just wouldn't do that for a platform with insignificant market share, which is great for Apple fans (the market share, not the malware). However, it's odd how this infection could happen in the first place, given how many hardcore Apple Mac fans know their machines are so secure and bulletproof that they don't need any security software...
View at TechPowerUp Main Site
So, now the criminals also know about all the sites one has visited, eroding user privacy even more. It looks like this malware has covered all the bases, but wait, there's more.it runs a script that copies information to a file called dump.txt regarding truecrypt data, Vidalia (TOR plugin for Firefox), your Safari browsing history, and .bash_history.


Additionally, it also looks for files matching "pthc", but it's not clear why, as Sophos reports:
Curiously, the Trojan also hunts for any files that match "pthc". It's unclear whether this is intended to uncover child abuse material or not (the phrase "pthc" is sometimes used on the internet to refer to pre-teen hardcore pornography).
This adds a really distasteful twist, doesn't it?
But how does a hapless Mac user know that their machine is infected? One of the first signs is sluggish performance and possibly extra noise from the fan on the graphics card. This is because the trojan harnesses the significant power available in today's GPU's to perform the Bitcoin mining. A mid to high end GPU can actually outperform any general purpose CPU, no matter how fast, by several orders of magnitude, which is very important when performing any cryptographic functions that require a lot of processing power, hence this particular hijack.
The trojan unsurprisingly comes as a payload within pirate software downloaded from unofficial sources. In this instance its been found in image editing application GraphicConverter v7.4, but is sure to be embedded in more dodgy software, along with improved [sic] versions of it, eventually. We wish to stress that the software house which sells GraphicConverter is innocent and is as much a victim as the unscrupulous user who downloads the hooky version.
This malware is obviously relatively sophisticated, judging by the number of nefarious functions it performs. This means that it could not have been trivial to write, test and debug, so therefore took significant time and resources of the criminals that wrote it. They just wouldn't do that for a platform with insignificant market share, which is great for Apple fans (the market share, not the malware). However, it's odd how this infection could happen in the first place, given how many hardcore Apple Mac fans know their machines are so secure and bulletproof that they don't need any security software...
View at TechPowerUp Main Site






