Raevenlord
News Editor
- Joined
- Aug 12, 2016
- Messages
- 3,755 (1.19/day)
- Location
- Portugal
| System Name | The Ryzening |
|---|---|
| Processor | AMD Ryzen 9 5900X |
| Motherboard | MSI X570 MAG TOMAHAWK |
| Cooling | Lian Li Galahad 360mm AIO |
| Memory | 32 GB G.Skill Trident Z F4-3733 (4x 8 GB) |
| Video Card(s) | Gigabyte RTX 3070 Ti |
| Storage | Boot: Transcend MTE220S 2TB, Kintson A2000 1TB, Seagate Firewolf Pro 14 TB |
| Display(s) | Acer Nitro VG270UP (1440p 144 Hz IPS) |
| Case | Lian Li O11DX Dynamic White |
| Audio Device(s) | iFi Audio Zen DAC |
| Power Supply | Seasonic Focus+ 750 W |
| Mouse | Cooler Master Masterkeys Lite L |
| Keyboard | Cooler Master Masterkeys Lite L |
| Software | Windows 10 x64 |
Thanks to AMD's incorporation of an ARM-based "AMD Secure Processor" in their upcoming ZEN micro-architecture, the company is poised to offer something competitor Intel's microprocessors yet don't: memory encryption. This processor, and its underlying technologies, could prove to be a stepping-stone for AMD towards regaining lost server market share. Essentially, because in a market ever more steered by cloud computing considerations, it allows for the client's data to be encrypted at every moment of the work chain. Assuming all works as intended, for the first time not even cloud providers, with either hypervisor-level privileges or even physical access to the servers, will be able to carry out any malicious actions against their clients.
One only has to consider the writing on the wall: Morgan Stanley predicts that by 2018, 30% of Microsoft's revenue will stem from its cloud services; Amazon Web Services (AWS) generated $7.88B in revenue on Q4 2015, up 69% over 2014; and worldwide spending on public cloud services by itself will grow from $70B in 2015 to an estimated $141B in 2019. Cloud computing is here to stay, and with security being as important as it is for some businesses, this is an important area of investment for AMD. This "AMD Secure Processor" will work on essentially two fronts: SME (Secure Memory Encryption) and SEV (Secure Encrypted Virtualization), backed by an hardware-based SHA (Secure Hash Algorithm).

According to AMD's Memory Encryption Whitepaper, SME works by leveraging the Secure Processor in encrypting data (using a 128-bit AES encryption key) when it is written to DRAM, effectively putting an end to the last redoubt of Cleartext-stored data. This becomes increasingly important when one considers the advent of NVDIMM (non volatile memory), which if left unencrypted, would be much more vulnerable to physical removal and subsequent cloning of its contents than currently employed solutions. This encryption key is randomly generated by the Secure Processor on each system reset, and is never accessible by any software running on the CPU cores. Furthermore, AMD states that the encryption impact on performance (namely, latency on memory accesses) is, quote, "very small", even when the entirety of the addressable memory is encrypted, but especially considering the Security Processor's ability to encrypt only specific memory pages, and not the entire amount of used RAM.
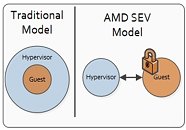
SEV, on the other hand, solves the problem with the traditional ring-based security system, where customer's code runs at a lower privilege level than the hypervisor. In essence, this means that in ring-based security, the hypervisor can have access to the guest's (ie., client's) data. With SEV, that will no longer be the case, isolating the hypervisor and the client's resources, as well as different client's workloads running on the same machine. Each of these workloads, as well as the hypervisor, will have their code and data tagged and separately encrypted, guaranteeing that each time the encrypted data is accessed by code with an incorrect encryption tag, all it sees is its encrypted state. SEV differs from SME in that in this case, the hypervisor must interact with the Secure Processor in order for the encryption to occur. It informs the Secure Processor that an encrypted VM (Virtual Machine) is going to run, and passes to the server's Secure Processor the needed certificates and exchange key which, in turn, allows the Secure Processor to load the appropriate, unique AES key.

With the ever-expanding computing requirements of businesses and customers worldwide being increasingly serviced by servers on the so-called cloud, the need for increased security becomes more and more of a concern for service-providers. According to The 2016 Global Cloud Data Security Study, 60% of IT professionals consider it to be more difficult to protect confidential or sensitive information in the cloud. At the same time, it's estimated that globally, 36% of organization's total IT and data processing needs are met by cloud resources. This is expected to increase to 45% over the next two years.
And with 86% of the study's respondents claiming encryption will become even more important over the next two years, this feature disparity between AMD and Intel's solutions could prove to be an ace up AMD's sleeve in regaining some of its lost server market share from its glory days.
View at TechPowerUp Main Site
One only has to consider the writing on the wall: Morgan Stanley predicts that by 2018, 30% of Microsoft's revenue will stem from its cloud services; Amazon Web Services (AWS) generated $7.88B in revenue on Q4 2015, up 69% over 2014; and worldwide spending on public cloud services by itself will grow from $70B in 2015 to an estimated $141B in 2019. Cloud computing is here to stay, and with security being as important as it is for some businesses, this is an important area of investment for AMD. This "AMD Secure Processor" will work on essentially two fronts: SME (Secure Memory Encryption) and SEV (Secure Encrypted Virtualization), backed by an hardware-based SHA (Secure Hash Algorithm).

According to AMD's Memory Encryption Whitepaper, SME works by leveraging the Secure Processor in encrypting data (using a 128-bit AES encryption key) when it is written to DRAM, effectively putting an end to the last redoubt of Cleartext-stored data. This becomes increasingly important when one considers the advent of NVDIMM (non volatile memory), which if left unencrypted, would be much more vulnerable to physical removal and subsequent cloning of its contents than currently employed solutions. This encryption key is randomly generated by the Secure Processor on each system reset, and is never accessible by any software running on the CPU cores. Furthermore, AMD states that the encryption impact on performance (namely, latency on memory accesses) is, quote, "very small", even when the entirety of the addressable memory is encrypted, but especially considering the Security Processor's ability to encrypt only specific memory pages, and not the entire amount of used RAM.
SEV, on the other hand, solves the problem with the traditional ring-based security system, where customer's code runs at a lower privilege level than the hypervisor. In essence, this means that in ring-based security, the hypervisor can have access to the guest's (ie., client's) data. With SEV, that will no longer be the case, isolating the hypervisor and the client's resources, as well as different client's workloads running on the same machine. Each of these workloads, as well as the hypervisor, will have their code and data tagged and separately encrypted, guaranteeing that each time the encrypted data is accessed by code with an incorrect encryption tag, all it sees is its encrypted state. SEV differs from SME in that in this case, the hypervisor must interact with the Secure Processor in order for the encryption to occur. It informs the Secure Processor that an encrypted VM (Virtual Machine) is going to run, and passes to the server's Secure Processor the needed certificates and exchange key which, in turn, allows the Secure Processor to load the appropriate, unique AES key.


With the ever-expanding computing requirements of businesses and customers worldwide being increasingly serviced by servers on the so-called cloud, the need for increased security becomes more and more of a concern for service-providers. According to The 2016 Global Cloud Data Security Study, 60% of IT professionals consider it to be more difficult to protect confidential or sensitive information in the cloud. At the same time, it's estimated that globally, 36% of organization's total IT and data processing needs are met by cloud resources. This is expected to increase to 45% over the next two years.
And with 86% of the study's respondents claiming encryption will become even more important over the next two years, this feature disparity between AMD and Intel's solutions could prove to be an ace up AMD's sleeve in regaining some of its lost server market share from its glory days.
View at TechPowerUp Main Site
Last edited by a moderator:









 Hope to keep you guys interested.
Hope to keep you guys interested.