Raevenlord
News Editor
- Joined
- Aug 12, 2016
- Messages
- 3,755 (1.19/day)
- Location
- Portugal
| System Name | The Ryzening |
|---|---|
| Processor | AMD Ryzen 9 5900X |
| Motherboard | MSI X570 MAG TOMAHAWK |
| Cooling | Lian Li Galahad 360mm AIO |
| Memory | 32 GB G.Skill Trident Z F4-3733 (4x 8 GB) |
| Video Card(s) | Gigabyte RTX 3070 Ti |
| Storage | Boot: Transcend MTE220S 2TB, Kintson A2000 1TB, Seagate Firewolf Pro 14 TB |
| Display(s) | Acer Nitro VG270UP (1440p 144 Hz IPS) |
| Case | Lian Li O11DX Dynamic White |
| Audio Device(s) | iFi Audio Zen DAC |
| Power Supply | Seasonic Focus+ 750 W |
| Mouse | Cooler Master Masterkeys Lite L |
| Keyboard | Cooler Master Masterkeys Lite L |
| Software | Windows 10 x64 |
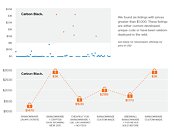
Carbon Black, a cybersecurity company that's been founded by former members of the U.S. government's elite team of offensive security hackers, has released a report detailing the continued rise of ransomware's impact, which served as the fire-starter for this piece. Carbon Black's Threat Analysis Unit (TAU) has found that ransomware is an increasingly prolific economical entity, bolstered by a 2,502% increase in sales in the dark web. As with every activity, legal or illegal, the economic footprint follows profit; and in ransomware's case, it's estimated it has yielded around $1 billion just this year. Ransomware even has the advantage of not requiring specialized computer skills, and can be quickly and brainlessly deployed in search of a quick buck.
Carbon Black reports that there are currently more than 6,300 ransomware marketplaces in the dark web, with over 45,000 different product listings, which range in price from $0.5 to $3K (the median price for a DIY ransomware package stands at roughly $10.5). Ransomware sellers are taking advantage of this burgeoning, "quick buck at anyone's expense" reasoning: some ransomware sellers are earning more than six figures yearly, sometimes even more than legitimate software companies. It's no surprise, however that the report points to technologies such as Bitcoin and the Tor network as being two of the most important enablers in this ransomware explosion, besides making it much more difficult for law enforcement agencies to, well, enforce the perpetrators.


To our Forum Dwellers: this piece is marked as an Editorial
There are two fundamental chains in the world of ransomware's creation and distribution: the kill chain and the supply chain.
The ransomware kill chain can be divided in five different modules: Creation > Distribution > Encryption > Payment > Command & Control. The entire kill chain can be distributed via DIU kits that contain all the necessary modules for payload deployment; more exotic solutions, however, may mix and match different authors' and services' codes to achieve a desired, specific effect.

Creation is easy to understand; it's the part of the chain where an author writes, tests, and maintains a piece of ransomware code. These can be written in an all-encompassing, mass-market way, targeting widespread vulnerabilities, or can be written specifically, as needed, for a targeted campaign. Higher levels of code customization naturally make the coding effort more expensive.
Distribution is the means by which ransomware actually reaches users' computers. This can be done via brute force, "spray and pray" methods, such as mail spamming, compromised websites, ads, social engineering, or targeted hacks - as we've seen with some high-profile business attacks, such as with WannaCry.

Encryption/Decryption is the module responsible for encrypting the users' data that will be ransomed - if a ransom is the objective, anyway. After this phase has been successful, usually there's a gaudy, nerve-chilling screen that alerts the user to the ransomed state of their private data, giving instructions for payment and - hopefully - eventual decryption.

Payment is pretty self-explanatory; though nowadays, the rise of cryptocurrencies have decreased the risk of discovery from the perpetrators, especially with the more privacy-focused coins such as Monero and ZCash. Whereas before, VISA or bank transfer payments could leave a trail for eventual perpetrator identification, nowadays it's much more difficult - and oft impossible - to identify the infection source.
The Command & Control module allows for remote control of the users' system and ransomed files, enabling end-to-end operations, and have been increasingly deployed in the wake of the RaaS (Ransomware as a Service) rise in popularity.
Ransomware supply chains can be differentiated in three tiers: Authors, RaaS, and Distributors.
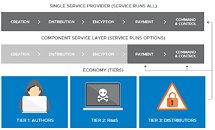
Authors are the weapon makers in the ransomware economy; they are responsible for the creation of new ransomware for sale, and usually have advanced coding skills that allow them to also provide ransomware platforms and/or charge others for training and support in ransomware coding. They can author specific parts of the ransomware kill chain (creation; distribution; encryption; payment; command & control) or develop all-encompassing, DIY packages that pack the entirety of the kill chain or allows users to code their own.
RaaS stands as a way for users to effortlessly distribute ransomware packages. It's usually controlled via a web portal with a GUI (Graphical User Interface) which basically removes all of the coding/deployment work from the user. Ransomware packages and access to these ransomware services can be free (with the service provider taking a cut of the users' successful ransomware attacks), or with an up-front payment which gives access to the needed software packages. The RaaS providers can take more than half the share of the ransomware profits, but some platforms take less than that (like Satan, one fo the more user friendly RaaS, which usually takes a 30% cut from profits, or even just 20%, in the case of Atom (previously known as Shark). These providers usually handle all the hassle of performing the ransomware campaign tracking, Bitcoin transaction monitoring, and Bitcoin distribution. These providers make use of their attack data to perfect and guide their subsequent attacks, based on machine infection success rate, payment rates, and other metrics. Thus, this is effectively "Hacking for Dummies", lowering the barrier of entry to almost laughable levels; no specialization or code knowledge is needed.
The third Tier, Distributors, is naturally collapsing under the weight of the RaaS providers, who offer basically the same service (and more) but with much less user intervention and an overall more automated process. The Distributors are the parts responsible for distributing and delivering ransomware attacks via spam, targeted hacks, or exploit kits
As to the future of ransomware and what it will mean for users of the world wide web and its increasingly important place in our lives, Carbon Black has a number of projections for the ransomware field as we enter 2018, which include:
As it stands, the ransomware economy is approaching cloud-service levels of ease-of-access and platform enablement. This, coupled with the fact that there will always be profits to be made so long as users are willing to pay the ransom - and surveys show a majority of users would be willing to pay the price - there will always be motivation towards ransomware usage. The RaaS philosophy has enabled authors to focus on authoring, distributors to focus on distributing, and users to simply press the proverbial red button in massively higher quantities than before, which is why ransomware is a booming economy. With increased specialization from the different players in the supply ad kill-chain and increased distribution numbers, the frequency and severity of attacks is only going to increase. Knowledge may not be the more effective way of combating this kind of attacks, but awareness is surely better than the alternative.
View at TechPowerUp Main Site
Carbon Black reports that there are currently more than 6,300 ransomware marketplaces in the dark web, with over 45,000 different product listings, which range in price from $0.5 to $3K (the median price for a DIY ransomware package stands at roughly $10.5). Ransomware sellers are taking advantage of this burgeoning, "quick buck at anyone's expense" reasoning: some ransomware sellers are earning more than six figures yearly, sometimes even more than legitimate software companies. It's no surprise, however that the report points to technologies such as Bitcoin and the Tor network as being two of the most important enablers in this ransomware explosion, besides making it much more difficult for law enforcement agencies to, well, enforce the perpetrators.



To our Forum Dwellers: this piece is marked as an Editorial
There are two fundamental chains in the world of ransomware's creation and distribution: the kill chain and the supply chain.
The ransomware kill chain can be divided in five different modules: Creation > Distribution > Encryption > Payment > Command & Control. The entire kill chain can be distributed via DIU kits that contain all the necessary modules for payload deployment; more exotic solutions, however, may mix and match different authors' and services' codes to achieve a desired, specific effect.

Creation is easy to understand; it's the part of the chain where an author writes, tests, and maintains a piece of ransomware code. These can be written in an all-encompassing, mass-market way, targeting widespread vulnerabilities, or can be written specifically, as needed, for a targeted campaign. Higher levels of code customization naturally make the coding effort more expensive.
Distribution is the means by which ransomware actually reaches users' computers. This can be done via brute force, "spray and pray" methods, such as mail spamming, compromised websites, ads, social engineering, or targeted hacks - as we've seen with some high-profile business attacks, such as with WannaCry.

Encryption/Decryption is the module responsible for encrypting the users' data that will be ransomed - if a ransom is the objective, anyway. After this phase has been successful, usually there's a gaudy, nerve-chilling screen that alerts the user to the ransomed state of their private data, giving instructions for payment and - hopefully - eventual decryption.

Payment is pretty self-explanatory; though nowadays, the rise of cryptocurrencies have decreased the risk of discovery from the perpetrators, especially with the more privacy-focused coins such as Monero and ZCash. Whereas before, VISA or bank transfer payments could leave a trail for eventual perpetrator identification, nowadays it's much more difficult - and oft impossible - to identify the infection source.
The Command & Control module allows for remote control of the users' system and ransomed files, enabling end-to-end operations, and have been increasingly deployed in the wake of the RaaS (Ransomware as a Service) rise in popularity.
Ransomware supply chains can be differentiated in three tiers: Authors, RaaS, and Distributors.

Authors are the weapon makers in the ransomware economy; they are responsible for the creation of new ransomware for sale, and usually have advanced coding skills that allow them to also provide ransomware platforms and/or charge others for training and support in ransomware coding. They can author specific parts of the ransomware kill chain (creation; distribution; encryption; payment; command & control) or develop all-encompassing, DIY packages that pack the entirety of the kill chain or allows users to code their own.
RaaS stands as a way for users to effortlessly distribute ransomware packages. It's usually controlled via a web portal with a GUI (Graphical User Interface) which basically removes all of the coding/deployment work from the user. Ransomware packages and access to these ransomware services can be free (with the service provider taking a cut of the users' successful ransomware attacks), or with an up-front payment which gives access to the needed software packages. The RaaS providers can take more than half the share of the ransomware profits, but some platforms take less than that (like Satan, one fo the more user friendly RaaS, which usually takes a 30% cut from profits, or even just 20%, in the case of Atom (previously known as Shark). These providers usually handle all the hassle of performing the ransomware campaign tracking, Bitcoin transaction monitoring, and Bitcoin distribution. These providers make use of their attack data to perfect and guide their subsequent attacks, based on machine infection success rate, payment rates, and other metrics. Thus, this is effectively "Hacking for Dummies", lowering the barrier of entry to almost laughable levels; no specialization or code knowledge is needed.


The third Tier, Distributors, is naturally collapsing under the weight of the RaaS providers, who offer basically the same service (and more) but with much less user intervention and an overall more automated process. The Distributors are the parts responsible for distributing and delivering ransomware attacks via spam, targeted hacks, or exploit kits
As to the future of ransomware and what it will mean for users of the world wide web and its increasingly important place in our lives, Carbon Black has a number of projections for the ransomware field as we enter 2018, which include:
- An increase in Linux systems targeting;
- Increasingly targeted ransomware attacks towards specific companies such as legal, healthcare, and tax preparers, and specific files, such as proprietary elements;
- Added capability to not only encrypt, but also exfiltrate files, so as to profit from both the ransom and black market sale of the exfiltrated data;
- Ransomware as a smokescreen and false-flag, hiding the true intentions behind the attack, like the Petya/NotPetya case;
- Ransomware as a backup to failures of more specific attacks, due to its easy-to-deploy nature;
- Increased usage of social media as a distributor, with social engineering efforts that lead users to knowingly share compromised links to reduce or eliminate their ransom;
- Persistence-based ransomware, which burrows in the users' system and re-encrypts data for another extortion effort - even more likely to take place in machines where previous ransom demands proved successful.
As it stands, the ransomware economy is approaching cloud-service levels of ease-of-access and platform enablement. This, coupled with the fact that there will always be profits to be made so long as users are willing to pay the ransom - and surveys show a majority of users would be willing to pay the price - there will always be motivation towards ransomware usage. The RaaS philosophy has enabled authors to focus on authoring, distributors to focus on distributing, and users to simply press the proverbial red button in massively higher quantities than before, which is why ransomware is a booming economy. With increased specialization from the different players in the supply ad kill-chain and increased distribution numbers, the frequency and severity of attacks is only going to increase. Knowledge may not be the more effective way of combating this kind of attacks, but awareness is surely better than the alternative.
View at TechPowerUp Main Site
Last edited:



