Raevenlord
News Editor
- Joined
- Aug 12, 2016
- Messages
- 3,755 (1.23/day)
- Location
- Portugal
| System Name | The Ryzening |
|---|---|
| Processor | AMD Ryzen 9 5900X |
| Motherboard | MSI X570 MAG TOMAHAWK |
| Cooling | Lian Li Galahad 360mm AIO |
| Memory | 32 GB G.Skill Trident Z F4-3733 (4x 8 GB) |
| Video Card(s) | Gigabyte RTX 3070 Ti |
| Storage | Boot: Transcend MTE220S 2TB, Kintson A2000 1TB, Seagate Firewolf Pro 14 TB |
| Display(s) | Acer Nitro VG270UP (1440p 144 Hz IPS) |
| Case | Lian Li O11DX Dynamic White |
| Audio Device(s) | iFi Audio Zen DAC |
| Power Supply | Seasonic Focus+ 750 W |
| Mouse | Cooler Master Masterkeys Lite L |
| Keyboard | Cooler Master Masterkeys Lite L |
| Software | Windows 10 x64 |
A Malwarebytes report calls attention to the latest occurrence in the inevitable trend that that ensues a particular security vulnerability being given coverage by the media. As users' attention to the vulnerability is heightened, so is their search for a solution, for a way to reduce the risk of exposition. Hence, users search for patches; and hence, some fake patches surface that take advantage of the more distracted, or less informed, of those who really just want to be left at peace.
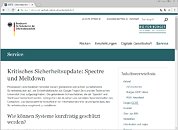
Case in point: Malwarebytes has identified a recently-registered domain that is particularly targeting German users (remember: you can be next; it's just a matter of Google translating the page for it be targeting you as well). The website is offering an information page with various links to external resources about Meltdown and Spectre and how it affects processors, and is affiliated with the German Federal Office for Information Security (BSI) - all good, right?
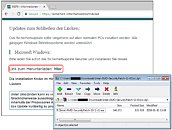
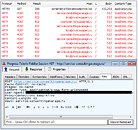
Expect it really isn't; its affiliation is only apparent, and this is an SSL-enabled phishing site that allows users to download a ZIP archive ("Intel-AMD-SecurityPatch-11-01bsi.zip") containing a so-called patch ("Intel-AMD-SecurityPatch-10-1-v1.exe"), which really is a piece of malware. Upon running it, users will infect themselves with Smoke Loader, a piece of malware that can retrieve additional payloads. Post-infection traffic shows the malicious file attempting to connect to various domains and sending encrypted information. So you think you're becoming less vulnerable, when in reality... Ah, the beauty of adding insult to injury.
View at TechPowerUp Main Site
Case in point: Malwarebytes has identified a recently-registered domain that is particularly targeting German users (remember: you can be next; it's just a matter of Google translating the page for it be targeting you as well). The website is offering an information page with various links to external resources about Meltdown and Spectre and how it affects processors, and is affiliated with the German Federal Office for Information Security (BSI) - all good, right?


Expect it really isn't; its affiliation is only apparent, and this is an SSL-enabled phishing site that allows users to download a ZIP archive ("Intel-AMD-SecurityPatch-11-01bsi.zip") containing a so-called patch ("Intel-AMD-SecurityPatch-10-1-v1.exe"), which really is a piece of malware. Upon running it, users will infect themselves with Smoke Loader, a piece of malware that can retrieve additional payloads. Post-infection traffic shows the malicious file attempting to connect to various domains and sending encrypted information. So you think you're becoming less vulnerable, when in reality... Ah, the beauty of adding insult to injury.

View at TechPowerUp Main Site





