Raevenlord
News Editor
- Joined
- Aug 12, 2016
- Messages
- 3,755 (1.18/day)
- Location
- Portugal
| System Name | The Ryzening |
|---|---|
| Processor | AMD Ryzen 9 5900X |
| Motherboard | MSI X570 MAG TOMAHAWK |
| Cooling | Lian Li Galahad 360mm AIO |
| Memory | 32 GB G.Skill Trident Z F4-3733 (4x 8 GB) |
| Video Card(s) | Gigabyte RTX 3070 Ti |
| Storage | Boot: Transcend MTE220S 2TB, Kintson A2000 1TB, Seagate Firewolf Pro 14 TB |
| Display(s) | Acer Nitro VG270UP (1440p 144 Hz IPS) |
| Case | Lian Li O11DX Dynamic White |
| Audio Device(s) | iFi Audio Zen DAC |
| Power Supply | Seasonic Focus+ 750 W |
| Mouse | Cooler Master Masterkeys Lite L |
| Keyboard | Cooler Master Masterkeys Lite L |
| Software | Windows 10 x64 |
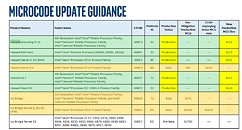
Via updated documents on its Microcode Revision guide, Intel has revealed that they have finally developed and started deploying microcode security updates for their Broadwell and Haswell-based microprocessors. The microcode update comes after a flurry of nearly platform-specific updates that aimed to mitigate known vulnerabilities in Intel's CPUs to the exploits known as Spectre and Meltdown.
While that's good news, Intel's patching odyssey still isn't over, by any means. According to Intel's documentation, the Spectre fixes for Sandy Bridge and Ivy Bridge are still in beta and are being tested by hardware partners, so that's two other architectures that still remain vulnerable. Of course, this discussion of who's vulnerable and isn't really can't be reduced to which architectures Intel has released its updates to. Users have to remember that the trickle-down process from Intel's patch validation and distribution through manufacturers to end users' systems is a morose one, and is also partially in the hands of sometimes not too tech-savy users. Time will tell if these flaws will have any major impact in some users or businesses.



View at TechPowerUp Main Site
While that's good news, Intel's patching odyssey still isn't over, by any means. According to Intel's documentation, the Spectre fixes for Sandy Bridge and Ivy Bridge are still in beta and are being tested by hardware partners, so that's two other architectures that still remain vulnerable. Of course, this discussion of who's vulnerable and isn't really can't be reduced to which architectures Intel has released its updates to. Users have to remember that the trickle-down process from Intel's patch validation and distribution through manufacturers to end users' systems is a morose one, and is also partially in the hands of sometimes not too tech-savy users. Time will tell if these flaws will have any major impact in some users or businesses.




View at TechPowerUp Main Site







