Raevenlord
News Editor
- Joined
- Aug 12, 2016
- Messages
- 3,755 (1.19/day)
- Location
- Portugal
| System Name | The Ryzening |
|---|---|
| Processor | AMD Ryzen 9 5900X |
| Motherboard | MSI X570 MAG TOMAHAWK |
| Cooling | Lian Li Galahad 360mm AIO |
| Memory | 32 GB G.Skill Trident Z F4-3733 (4x 8 GB) |
| Video Card(s) | Gigabyte RTX 3070 Ti |
| Storage | Boot: Transcend MTE220S 2TB, Kintson A2000 1TB, Seagate Firewolf Pro 14 TB |
| Display(s) | Acer Nitro VG270UP (1440p 144 Hz IPS) |
| Case | Lian Li O11DX Dynamic White |
| Audio Device(s) | iFi Audio Zen DAC |
| Power Supply | Seasonic Focus+ 750 W |
| Mouse | Cooler Master Masterkeys Lite L |
| Keyboard | Cooler Master Masterkeys Lite L |
| Software | Windows 10 x64 |
Intel on their latest Microcode Revision Guidance Guide has apparently stopped development of mitigations for some of its processor families that still haven't been updated to combat the threat of Spectre. The odyssey for the return to form of security on Intel products has been a steep, and a slow one, as the company has struggled to deploy mitigations for speculative code execution on its processor families that run it. Updates for some families of products, however - such as Penryn, Wolfdale, Bloomfield and Yorkfield, among others - are apparently not going to get an update at all.


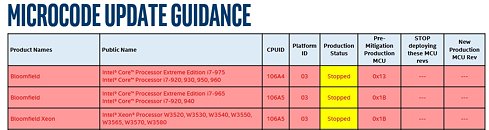
The state on the "Production Status" for mitigations for these families has been updated from their "Planning" or "Pre-Beta" state that can be found on Intel's March 6th 2018 Microcode Revision Guidance Guide, to a new, previously unseen "Stopped" state in their latest version of the Guide, published on April 2nd.
The reasons for this "Stopped" state, as Intel puts it, are that "After a comprehensive investigation of the microarchitectures and microcode capabilities for these products, Intel has determined to not release microcode updates for these products for one or more reasons including, but not limited to the following: a) Micro - architectural characteristics that preclude a practical implementation of features mitigating Variant 2 (CVE - 2017 - 5715 ); b) Limited Commercially Available System Software support; c) Based on customer inputs, most of these products are implemented as "closed systems" and therefore are expected to have a lower likelihood of exposure to these vulnerabilities."
If any one system with this vulnerability does get exploited via a method that could be averted by the implementation of a now "Stopped" patch, though, Intel should start reeling in those lawyers back into the fold.
View at TechPowerUp Main Site


The state on the "Production Status" for mitigations for these families has been updated from their "Planning" or "Pre-Beta" state that can be found on Intel's March 6th 2018 Microcode Revision Guidance Guide, to a new, previously unseen "Stopped" state in their latest version of the Guide, published on April 2nd.

The reasons for this "Stopped" state, as Intel puts it, are that "After a comprehensive investigation of the microarchitectures and microcode capabilities for these products, Intel has determined to not release microcode updates for these products for one or more reasons including, but not limited to the following: a) Micro - architectural characteristics that preclude a practical implementation of features mitigating Variant 2 (CVE - 2017 - 5715 ); b) Limited Commercially Available System Software support; c) Based on customer inputs, most of these products are implemented as "closed systems" and therefore are expected to have a lower likelihood of exposure to these vulnerabilities."
If any one system with this vulnerability does get exploited via a method that could be averted by the implementation of a now "Stopped" patch, though, Intel should start reeling in those lawyers back into the fold.
View at TechPowerUp Main Site





