- Joined
- Jul 1, 2014
- Messages
- 3,718 (0.96/day)
Magecart is a relatively new online exploit group that has been in the news recently for affecting British Airways, and Ticketmaster in the recent past months. This hithero-unrecognized group uses a web-based card skimmer script by injecting a precious few lines of malicious code in a website, to then steal sensitive data that customers enter in the payment sections of said affected websites. Two large digital threat management outfits, RiskIQ and Volexity, today released their reports on how Newegg was similarly affected during the time period of August 13, 2018 through September 18, 2018, and what this means to users who may have performed a transaction on the website during this period.
In particular, Newegg.com was affected when the criminals behind Magecart registed the neweggstats.com domain (now inactive) via domain provider Namecheap. As RiskIQ points out, this was soon changed to navigate to the 217.23.4.11 IP address, which is a Magecart server that was used to receive and store all collected user data from the compromise that happened since. A fake certificate was issued to add a layer of legitimacy to the domain, as seen below. Be sure to read past the break to find out more details, and also what the bottom line is for affected users.


Voletix at this point was able to spot malicious JavaScript code limited to the secure.newegg.com page, which presented itself during the checkout stage of transactions done on Newegg. This code, seen below, only appeared once- during the billing information section- but was enough to collect user data including name, address, and also payment details which was then sent over to the drop server mentioned above.

Both agencies mention that the first time the hack was active was August 14, and the first confirmed confirmed attack took place on August 16. The manner of this compromise was identical to how Magecart affected other companies before. If anything, the attackers managed to make their code more efficient by needing only 8 lines of code here compared to the 22 lines they used with British Airways. The Volexity report, cited below, shares more technical information on how the attack works if you were so interested. The malicious code was removed on September 18, after Newegg received word of it and took some action. The company has since put out a short statement on social media acknowledging the attack, with more relevant details sent out to potentially affected users. If you or anyone you know received this email, please share it with us so we may update this story accordingly.
As it stands, this web-based skimmer was active for over a month and worked on both the desktop and mobile websites. There is no word yet on whether the Newegg mobile apps were similarly affected. This is certainly not good news to anyone, especially at a time when new hardware may have resulted in transactions in the affected period. Newegg is a giant e-tailer in the PC DIY industry, with over 50 million monthly visits. Both RiskIQ and Volexity warn that every one who has had a transaction on the website in the affected time period should keep an eye on their credit report (if appropriate), and work on re-issuing the form of payment used for said transaction(s). For example, if you used a credit card then talk to you bank to get that cancelled and have them issue you a new card as soon as possible. Magecart, as with other JavaScript-based criminal tools, are showing no signs of slowing down given the relatively simple attack strategy, and hopefully not many of us end up victims.
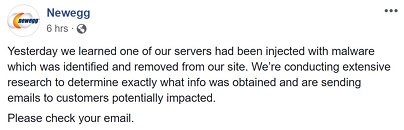
[Update: September 19, 2018- TechPowerUp member xkm1948 was kind enough to share a screenshot of the email he received from Newegg, which can be seen below]

View at TechPowerUp Main Site
In particular, Newegg.com was affected when the criminals behind Magecart registed the neweggstats.com domain (now inactive) via domain provider Namecheap. As RiskIQ points out, this was soon changed to navigate to the 217.23.4.11 IP address, which is a Magecart server that was used to receive and store all collected user data from the compromise that happened since. A fake certificate was issued to add a layer of legitimacy to the domain, as seen below. Be sure to read past the break to find out more details, and also what the bottom line is for affected users.


Voletix at this point was able to spot malicious JavaScript code limited to the secure.newegg.com page, which presented itself during the checkout stage of transactions done on Newegg. This code, seen below, only appeared once- during the billing information section- but was enough to collect user data including name, address, and also payment details which was then sent over to the drop server mentioned above.

Both agencies mention that the first time the hack was active was August 14, and the first confirmed confirmed attack took place on August 16. The manner of this compromise was identical to how Magecart affected other companies before. If anything, the attackers managed to make their code more efficient by needing only 8 lines of code here compared to the 22 lines they used with British Airways. The Volexity report, cited below, shares more technical information on how the attack works if you were so interested. The malicious code was removed on September 18, after Newegg received word of it and took some action. The company has since put out a short statement on social media acknowledging the attack, with more relevant details sent out to potentially affected users. If you or anyone you know received this email, please share it with us so we may update this story accordingly.

As it stands, this web-based skimmer was active for over a month and worked on both the desktop and mobile websites. There is no word yet on whether the Newegg mobile apps were similarly affected. This is certainly not good news to anyone, especially at a time when new hardware may have resulted in transactions in the affected period. Newegg is a giant e-tailer in the PC DIY industry, with over 50 million monthly visits. Both RiskIQ and Volexity warn that every one who has had a transaction on the website in the affected time period should keep an eye on their credit report (if appropriate), and work on re-issuing the form of payment used for said transaction(s). For example, if you used a credit card then talk to you bank to get that cancelled and have them issue you a new card as soon as possible. Magecart, as with other JavaScript-based criminal tools, are showing no signs of slowing down given the relatively simple attack strategy, and hopefully not many of us end up victims.
[Update: September 19, 2018- TechPowerUp member xkm1948 was kind enough to share a screenshot of the email he received from Newegg, which can be seen below]

View at TechPowerUp Main Site




