- Joined
- Oct 9, 2007
- Messages
- 47,878 (7.38/day)
- Location
- Dublin, Ireland
| System Name | RBMK-1000 |
|---|---|
| Processor | AMD Ryzen 7 5700G |
| Motherboard | Gigabyte B550 AORUS Elite V2 |
| Cooling | DeepCool Gammax L240 V2 |
| Memory | 2x 16GB DDR4-3200 |
| Video Card(s) | Galax RTX 4070 Ti EX |
| Storage | Samsung 990 1TB |
| Display(s) | BenQ 1440p 60 Hz 27-inch |
| Case | Corsair Carbide 100R |
| Audio Device(s) | ASUS SupremeFX S1220A |
| Power Supply | Cooler Master MWE Gold 650W |
| Mouse | ASUS ROG Strix Impact |
| Keyboard | Gamdias Hermes E2 |
| Software | Windows 11 Pro |
Wacom is a brand graphics artists swear by, thanks to its near monopoly over the pen-digitizer tablet market. These are essentially input devices in which convert pen-like input on a surface to 2D graphics on the screen, which high precision. Software engineer Robert Heaton discovered that the driver of Wacom tablets leak information on every application you open, to an entity that's using Google Analytics to collect the data.
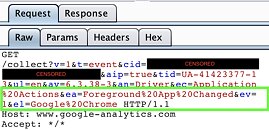
Heaton used Wireshark to first detect that his Wacom's driver is sending data packets to Google Analytics by monitoring its DNS lookups. The payload of data sent to the analytics website was encrypted by TLS. He then set up an internal proxy using Burp Suite that convinced the Wacom driver that it is sending data over a secure connection, and intercepted its payload. It was then discovered that Wacom driver tracks every application its users open (and not just applications of interest to the company). The company's EULA don't seek even implicit consent to collect this data, and it presents a big privacy challenge. Heaton argues that what if this could be used by Wacom employees to, say, discover that Valve software is working on "Half Life 3," by querying its data heap for executables that sound like "Half Life 3"? Find a fascinating technical run down of Heaton's discovery on his blog.

View at TechPowerUp Main Site
Heaton used Wireshark to first detect that his Wacom's driver is sending data packets to Google Analytics by monitoring its DNS lookups. The payload of data sent to the analytics website was encrypted by TLS. He then set up an internal proxy using Burp Suite that convinced the Wacom driver that it is sending data over a secure connection, and intercepted its payload. It was then discovered that Wacom driver tracks every application its users open (and not just applications of interest to the company). The company's EULA don't seek even implicit consent to collect this data, and it presents a big privacy challenge. Heaton argues that what if this could be used by Wacom employees to, say, discover that Valve software is working on "Half Life 3," by querying its data heap for executables that sound like "Half Life 3"? Find a fascinating technical run down of Heaton's discovery on his blog.


View at TechPowerUp Main Site






 .
.