- Joined
- Oct 9, 2007
- Messages
- 47,322 (7.52/day)
- Location
- Hyderabad, India
| System Name | RBMK-1000 |
|---|---|
| Processor | AMD Ryzen 7 5700G |
| Motherboard | ASUS ROG Strix B450-E Gaming |
| Cooling | DeepCool Gammax L240 V2 |
| Memory | 2x 8GB G.Skill Sniper X |
| Video Card(s) | Palit GeForce RTX 2080 SUPER GameRock |
| Storage | Western Digital Black NVMe 512GB |
| Display(s) | BenQ 1440p 60 Hz 27-inch |
| Case | Corsair Carbide 100R |
| Audio Device(s) | ASUS SupremeFX S1220A |
| Power Supply | Cooler Master MWE Gold 650W |
| Mouse | ASUS ROG Strix Impact |
| Keyboard | Gamdias Hermes E2 |
| Software | Windows 11 Pro |
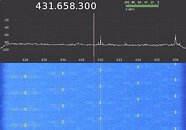
Thursday we brought you a story of an improbable but ingenious cybersecurity attack vector called Air-ViBER, which uses fan vibrations to transmit data to a nearby listening device in an air-gapped environment. Another team of researchers, led by Mikhail Davidov and Baron Oldenburg, developed an equally ingenious but more insidious attack vector - rapid manipulation of clock speeds of an AMD Radeon Pro WX3100 GPU to turn it into a tunable radio transmitter; and ferrying data off as inaudible and invisible RF transmissions. The graphics card itself works as a radio transmitter, the computer needn't have a WLAN device.
What's worse, the signal has an impressive 50-foot (15.2 m) range, can pass through walls, and can have a far higher data-rate than the fan vibration hack. Even worse, the attack doesn't require any special hacks of the GPU driver or physical modification of the graphics card in any way - only a tool that can manipulate its clock speeds (any overclocking software can do that). Luckily, overclocking tools are privileged applications (requiring ring-0 access), and in most machines it springs up a UAC gate unless the overclocking software installs a driver and service that runs in the background (this installation requires a UAC authorization in the first place). If someone managed to install privileged software on your computer, you have bigger problems than a graphics card that likes to sing. Find technical details of the hack here, and a video presentation here.
View at TechPowerUp Main Site
What's worse, the signal has an impressive 50-foot (15.2 m) range, can pass through walls, and can have a far higher data-rate than the fan vibration hack. Even worse, the attack doesn't require any special hacks of the GPU driver or physical modification of the graphics card in any way - only a tool that can manipulate its clock speeds (any overclocking software can do that). Luckily, overclocking tools are privileged applications (requiring ring-0 access), and in most machines it springs up a UAC gate unless the overclocking software installs a driver and service that runs in the background (this installation requires a UAC authorization in the first place). If someone managed to install privileged software on your computer, you have bigger problems than a graphics card that likes to sing. Find technical details of the hack here, and a video presentation here.

View at TechPowerUp Main Site





