- Joined
- Oct 9, 2007
- Messages
- 47,878 (7.38/day)
- Location
- Dublin, Ireland
| System Name | RBMK-1000 |
|---|---|
| Processor | AMD Ryzen 7 5700G |
| Motherboard | Gigabyte B550 AORUS Elite V2 |
| Cooling | DeepCool Gammax L240 V2 |
| Memory | 2x 16GB DDR4-3200 |
| Video Card(s) | Galax RTX 4070 Ti EX |
| Storage | Samsung 990 1TB |
| Display(s) | BenQ 1440p 60 Hz 27-inch |
| Case | Corsair Carbide 100R |
| Audio Device(s) | ASUS SupremeFX S1220A |
| Power Supply | Cooler Master MWE Gold 650W |
| Mouse | ASUS ROG Strix Impact |
| Keyboard | Gamdias Hermes E2 |
| Software | Windows 11 Pro |
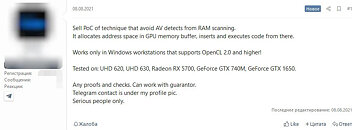
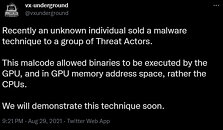
Cybercriminals have innovated a way to store malware code inside GPU dedicated memory (video memory), and execute code directly from there. Execution from video memory may not be new, but they've mostly been confined to the academic space, and unrefined. This would be the first time a proof-of-concept of a working tool that injects executables to video memory, surfaced on a hacker forum.
The tool relies on OpenCL 2.0, and its developers claim to have successfully tested it on Intel Gen9, AMD RDNA, NVIDIA Kepler, and NVIDIA Turing graphics architectures (i.e. UHD 620, UHD 630, Radeon RX 5700, GeForce GTX 740M, and GTX 1650). What makes this ingenious is that the malware binary is stored entirely in GPU memory address-space and is executed by the GPU, rather than the CPUs. Conventional anti-malware software are only known to scan the system memory, disks, and network traffic for malware; but not video memory. Hopefully this will change.
View at TechPowerUp Main Site
The tool relies on OpenCL 2.0, and its developers claim to have successfully tested it on Intel Gen9, AMD RDNA, NVIDIA Kepler, and NVIDIA Turing graphics architectures (i.e. UHD 620, UHD 630, Radeon RX 5700, GeForce GTX 740M, and GTX 1650). What makes this ingenious is that the malware binary is stored entirely in GPU memory address-space and is executed by the GPU, rather than the CPUs. Conventional anti-malware software are only known to scan the system memory, disks, and network traffic for malware; but not video memory. Hopefully this will change.


View at TechPowerUp Main Site




 You can at least buy some uranium glassware. Just be sure to aim for the brain bucket!
You can at least buy some uranium glassware. Just be sure to aim for the brain bucket!
