Raevenlord
News Editor
- Joined
- Aug 12, 2016
- Messages
- 3,755 (1.18/day)
- Location
- Portugal
| System Name | The Ryzening |
|---|---|
| Processor | AMD Ryzen 9 5900X |
| Motherboard | MSI X570 MAG TOMAHAWK |
| Cooling | Lian Li Galahad 360mm AIO |
| Memory | 32 GB G.Skill Trident Z F4-3733 (4x 8 GB) |
| Video Card(s) | Gigabyte RTX 3070 Ti |
| Storage | Boot: Transcend MTE220S 2TB, Kintson A2000 1TB, Seagate Firewolf Pro 14 TB |
| Display(s) | Acer Nitro VG270UP (1440p 144 Hz IPS) |
| Case | Lian Li O11DX Dynamic White |
| Audio Device(s) | iFi Audio Zen DAC |
| Power Supply | Seasonic Focus+ 750 W |
| Mouse | Cooler Master Masterkeys Lite L |
| Keyboard | Cooler Master Masterkeys Lite L |
| Software | Windows 10 x64 |
If you've deployed an Asustor-made NAS (Network Attached Storage) to access your treasure trove of files across the wires of the Internet, you should disconnect it it from the Internet as soon as possible. A number of Asustor users have taken to Reddit and the company's forums, claiming their Asustor-bound files have been claimed and encrypted by a ransomware attack through a Deadbolt payload. This is the same ransomware that wreaked havoc with QNAP's NAS devices a while back.
The attack infects the user's NAS and proceeds to encrypt its contents, leaving each user with a message pointing towards a unique Bitcoin address. The offer: receive the decryption key in exchange for 0.03 Bitcoin (~$1,102, ~€976) - the same value asked at the time of the QNAP attack. Interestingly, Asustor doesn't seem to have received the same offer the perpetrators put forward to QNAP: 5 Bitcoin (~$183,906, ~€162,267) in return for information for the exploit data (€162,799) - or a universal decryption key for all affected users for 50 Bitcoin (~$1,8 million). That last bit there serves to put pressure on the company to pay up for the affected users, which could themselves pressure the company to take the deal.
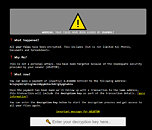

For now, Asustor hasn't issued any guidance to affected users other than safely powering-off and disconnecting their NAS from the networks until the company releases a fix (which form exactly this fix will take is a mystery). Users should also be contacted by an Asustor technician after they fill out a web form. It's speculated that the hackers gained access to the Asustor NAS products via their EZ Connect utility. And apparently Asustor's own product demo was hosted in a now compromised storage solution, as its Asustor Data Master (ADM) Live Demo has been brought down.
An official listing of affected products isn't currently available. However, affected users have collated a listing of sorts according to their own reports. In them, affected models so far seem to be restricted to the AS5304T, AS6204T, AS6404T, AS5104T and AS7004T NAS devices. Others, such as the AS5004T, AS6602T, AS-6210T-4K and AS6102T, are (at least so far) free of infection reports. Users within the forums are recommending that other Asustor-deploying consumers disable the EZ Connect utility, automatic updates and SSH, alongside blocking all NAS ports and only allowing connections from within the users' network. In this case, it's better to be safe than sorry: until a list of vulnerable devices is shared by Asustor, it's best to assume all models are vulnerable.
For users who had their 2-bay NAS setup in RAID-1, there's now an unofficial tutorial requiring a Linux-bound PC that aims to help you recover your encrypted files.
View at TechPowerUp Main Site | Source
The attack infects the user's NAS and proceeds to encrypt its contents, leaving each user with a message pointing towards a unique Bitcoin address. The offer: receive the decryption key in exchange for 0.03 Bitcoin (~$1,102, ~€976) - the same value asked at the time of the QNAP attack. Interestingly, Asustor doesn't seem to have received the same offer the perpetrators put forward to QNAP: 5 Bitcoin (~$183,906, ~€162,267) in return for information for the exploit data (€162,799) - or a universal decryption key for all affected users for 50 Bitcoin (~$1,8 million). That last bit there serves to put pressure on the company to pay up for the affected users, which could themselves pressure the company to take the deal.


For now, Asustor hasn't issued any guidance to affected users other than safely powering-off and disconnecting their NAS from the networks until the company releases a fix (which form exactly this fix will take is a mystery). Users should also be contacted by an Asustor technician after they fill out a web form. It's speculated that the hackers gained access to the Asustor NAS products via their EZ Connect utility. And apparently Asustor's own product demo was hosted in a now compromised storage solution, as its Asustor Data Master (ADM) Live Demo has been brought down.
An official listing of affected products isn't currently available. However, affected users have collated a listing of sorts according to their own reports. In them, affected models so far seem to be restricted to the AS5304T, AS6204T, AS6404T, AS5104T and AS7004T NAS devices. Others, such as the AS5004T, AS6602T, AS-6210T-4K and AS6102T, are (at least so far) free of infection reports. Users within the forums are recommending that other Asustor-deploying consumers disable the EZ Connect utility, automatic updates and SSH, alongside blocking all NAS ports and only allowing connections from within the users' network. In this case, it's better to be safe than sorry: until a list of vulnerable devices is shared by Asustor, it's best to assume all models are vulnerable.
For users who had their 2-bay NAS setup in RAID-1, there's now an unofficial tutorial requiring a Linux-bound PC that aims to help you recover your encrypted files.
View at TechPowerUp Main Site | Source






