T0@st
News Editor
- Joined
- Mar 7, 2023
- Messages
- 2,077 (3.13/day)
- Location
- South East, UK
MSI suffered a massive data breach at the start of April and the Taiwanese electronics company promptly alerted its customers about the cyberattack on its "information systems." A few days later it emerged that a relatively young ransomware group "Money Message" was behind the hacking effort - these cybercriminals stated that they had infiltrated MSI's internal network. Gang members proceeded to acquire sensitive company files, database information and source code. At the time, Money Message demanded that MSI pay them a ransom of $4 million, with the added threat of stolen data getting leaked to the general public on the internet (in the event of MSI failing to pay up).
Money Message has this week claimed that MSI has refused to meet their demands - as a result, an upload of stolen data started on Thursday with files appearing on the group's own website, and spreading to the dark web soon after. Binarly, a cybersecurity firm, has since analyzed the leaked files and discovered the presence of many private code signing keys within the breached data dump. Alex Matrosov, Binarly's CEO states via Twitter: "Recently, MSI USA announced a significant data breach. The data has now been made public, revealing a vast number of private keys that could affect numerous devices. FW Image Signing Keys: 57 products (and) Intel Boot Guard BPM/KM Keys: 166 products." Binary has provided a list of affected MSI devices (gaming laptops & mobile workstations) on their GitHub page.



PC Magazine UK asked Matrosov for a few extra details, he then explained the significance of the private key leak: "The signing keys for firmware image allow an attacker to craft malicious firmware updates and it can be delivered through normal BIOS update processes with MSI update tools." Cybercriminals can create and sign malware disguised as MSI-related software, as well as fake and malicious firmware. Matrosov claims that customer-focused attacks could be delivered "as a second stage payload" through phishing attempts (email or website-based) - it is possible that anti-virus software will not flag these attacks due to the usage of official MSI signing keys. Binarly has also discovered that an Intel hardware security tool could be compromised by cybercriminals: "Digging deeper into the aftermath of the MSI USA data breach and its impact on the industry. Leaked Intel Boot Guard keys from MSI are affecting many different device vendors, including Intel, Lenovo, Supermicro SMCI, and many others industry-wide."
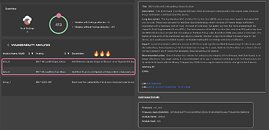
Matrosov's latest update on Twitter states: "Confirmed, Intel OEM private key leaked, causing an impact on the entire ecosystem. It appears that Intel Boot Guard may not be effective on certain devices based on the 11th Tiger Lake, 12th Adler Lake, and 13th Raptor Lake. Our investigation is ongoing, stay tuned for updates."
Mark Ermolov, an independent researcher of Intel Security systems, also interjected with his findings yesterday: "It seems this leak affects not only Intel Boot Guard technology, but all OEM signing-based mechanisms in CSME, such as OEM unlock (Orange Unlock), ISH firmware, SMIP and others."
View at TechPowerUp Main Site | Source
Money Message has this week claimed that MSI has refused to meet their demands - as a result, an upload of stolen data started on Thursday with files appearing on the group's own website, and spreading to the dark web soon after. Binarly, a cybersecurity firm, has since analyzed the leaked files and discovered the presence of many private code signing keys within the breached data dump. Alex Matrosov, Binarly's CEO states via Twitter: "Recently, MSI USA announced a significant data breach. The data has now been made public, revealing a vast number of private keys that could affect numerous devices. FW Image Signing Keys: 57 products (and) Intel Boot Guard BPM/KM Keys: 166 products." Binary has provided a list of affected MSI devices (gaming laptops & mobile workstations) on their GitHub page.




PC Magazine UK asked Matrosov for a few extra details, he then explained the significance of the private key leak: "The signing keys for firmware image allow an attacker to craft malicious firmware updates and it can be delivered through normal BIOS update processes with MSI update tools." Cybercriminals can create and sign malware disguised as MSI-related software, as well as fake and malicious firmware. Matrosov claims that customer-focused attacks could be delivered "as a second stage payload" through phishing attempts (email or website-based) - it is possible that anti-virus software will not flag these attacks due to the usage of official MSI signing keys. Binarly has also discovered that an Intel hardware security tool could be compromised by cybercriminals: "Digging deeper into the aftermath of the MSI USA data breach and its impact on the industry. Leaked Intel Boot Guard keys from MSI are affecting many different device vendors, including Intel, Lenovo, Supermicro SMCI, and many others industry-wide."

Matrosov's latest update on Twitter states: "Confirmed, Intel OEM private key leaked, causing an impact on the entire ecosystem. It appears that Intel Boot Guard may not be effective on certain devices based on the 11th Tiger Lake, 12th Adler Lake, and 13th Raptor Lake. Our investigation is ongoing, stay tuned for updates."
Mark Ermolov, an independent researcher of Intel Security systems, also interjected with his findings yesterday: "It seems this leak affects not only Intel Boot Guard technology, but all OEM signing-based mechanisms in CSME, such as OEM unlock (Orange Unlock), ISH firmware, SMIP and others."
View at TechPowerUp Main Site | Source