- Joined
- Aug 19, 2017
- Messages
- 2,753 (1.01/day)
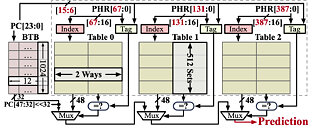
Researchers from the University of California, San Diego, have unveiled a significant security vulnerability affecting Intel Raptor Lake and Alder Lake processors. The newly discovered flaw, dubbed "Indirector," exposes weaknesses in the Indirect Branch Predictor (IBP) and Branch Target Buffer (BTB), potentially allowing attackers to execute precise Branch Target Injection (BTI) attacks. The published study provides a detailed look into the intricate structures of the IBP and BTB within recent Intel processors, showcasing Spectre-style attach. For the first time, researchers have mapped out the size, structure, and precise functions governing index and tag hashing in these critical components. Particularly concerning is the discovery of previously unknown gaps in Intel's hardware defenses, including IBPB, IBRS, and STIBP. These findings suggest that even the latest security measures may be insufficient to protect against sophisticated attacks.
The research team developed a tool called "iBranch Locator," which can efficiently identify and manipulate specific branches within the IBP. This tool enables highly precise BTI attacks, potentially compromising security across various scenarios, including cross-process and cross-privilege environments. One of the most alarming implications of this vulnerability is its ability to bypass Address Space Layout Randomization (ASLR), a crucial security feature in modern operating systems. By exploiting the IBP and BTB, attackers could potentially break ASLR protections, exposing systems to a wide range of security threats. Experts recommend several mitigation strategies, including more aggressive use of Intel's IBPB (Indirect Branch Prediction Barrier) feature. However, the performance impact of this solution—up to 50% in some cases—makes it impractical for frequent domain transitions, such as those in browsers and sandboxes. In a statement for Tom's Hardware, Intel noted the following: "Intel reviewed the report submitted by academic researchers and determined previous mitigation guidance provided for issues such as IBRS, eIBRS and BHI are effective against this new research and no new mitigations or guidance is required."

The company was notified in February and had room to fix it. Intel also notified its system vendors, so the security layers protecting against this are in place. Here is the BHI mitigation, and here is the IBRS/eIBRS mitigation.
View at TechPowerUp Main Site | Source
The research team developed a tool called "iBranch Locator," which can efficiently identify and manipulate specific branches within the IBP. This tool enables highly precise BTI attacks, potentially compromising security across various scenarios, including cross-process and cross-privilege environments. One of the most alarming implications of this vulnerability is its ability to bypass Address Space Layout Randomization (ASLR), a crucial security feature in modern operating systems. By exploiting the IBP and BTB, attackers could potentially break ASLR protections, exposing systems to a wide range of security threats. Experts recommend several mitigation strategies, including more aggressive use of Intel's IBPB (Indirect Branch Prediction Barrier) feature. However, the performance impact of this solution—up to 50% in some cases—makes it impractical for frequent domain transitions, such as those in browsers and sandboxes. In a statement for Tom's Hardware, Intel noted the following: "Intel reviewed the report submitted by academic researchers and determined previous mitigation guidance provided for issues such as IBRS, eIBRS and BHI are effective against this new research and no new mitigations or guidance is required."


The company was notified in February and had room to fix it. Intel also notified its system vendors, so the security layers protecting against this are in place. Here is the BHI mitigation, and here is the IBRS/eIBRS mitigation.
View at TechPowerUp Main Site | Source



