- Joined
- Aug 20, 2007
- Messages
- 21,542 (3.40/day)
| System Name | Pioneer |
|---|---|
| Processor | Ryzen R9 9950X |
| Motherboard | GIGABYTE Aorus Elite X670 AX |
| Cooling | Noctua NH-D15 + A whole lotta Sunon and Corsair Maglev blower fans... |
| Memory | 64GB (4x 16GB) G.Skill Flare X5 @ DDR5-6000 CL30 |
| Video Card(s) | XFX RX 7900 XTX Speedster Merc 310 |
| Storage | Intel 905p Optane 960GB boot, +2x Crucial P5 Plus 2TB PCIe 4.0 NVMe SSDs |
| Display(s) | 55" LG 55" B9 OLED 4K Display |
| Case | Thermaltake Core X31 |
| Audio Device(s) | TOSLINK->Schiit Modi MB->Asgard 2 DAC Amp->AKG Pro K712 Headphones or HDMI->B9 OLED |
| Power Supply | FSP Hydro Ti Pro 850W |
| Mouse | Logitech G305 Lightspeed Wireless |
| Keyboard | WASD Code v3 with Cherry Green keyswitches + PBT DS keycaps |
| Software | Gentoo Linux x64 / Windows 11 Enterprise IoT 2024 |
After last month's WannaCry outbreak (which persisted in its effects as recently as last week), we now have a new variant of ransomware infecting PCs across Europe. The outbreak seems centered in Ukraine, where several government facilities and critical pieces of infrastructure have been shutdown due to the attacks. The Ukrainian government seemed almost defiantly optimistic, posting this decidedly awesome response to twitter during the attack.
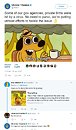
As if to signify not all is well, the attack has been widespread enough to even effect the radiation monitoring systems at Chernobyl, which have been reportedly switched to "manual mode" following an infection.
There are concerns that the ransomware could spread, and by the time this article was written, reports have already come in of infection across the Ukrainian borders, including in Denmark (with shipping conglomerate Maersk hit), and even isolated reports as far away as Russia and the USA.
The Director of Global Research for Kaspersky Labs, Costin Raiu, reports that the ransomware has made the most impact in the Ukraine, with the Russian Federation coming in at second. Poland takes third place, followed by Italy and then Germany. The infection is obviously spreading actively, so this list may not be accurate for long. One hopes it will not morph into a global outbreak.
UPDATE 5:45PM PST: As of this time, the network has hit the USA full force and is currently being covered on US news services. See the ABC news source for details.
The bitcoin wallet associated with this attack has already garnered more than 3.5 BTC at time of this writing, meaning at least some of the ransoms are being paid. The infection vector appears to be a compromised accounting software auto-update used common to most of the infected companies.
View at TechPowerUp Main Site

As if to signify not all is well, the attack has been widespread enough to even effect the radiation monitoring systems at Chernobyl, which have been reportedly switched to "manual mode" following an infection.
There are concerns that the ransomware could spread, and by the time this article was written, reports have already come in of infection across the Ukrainian borders, including in Denmark (with shipping conglomerate Maersk hit), and even isolated reports as far away as Russia and the USA.
The Director of Global Research for Kaspersky Labs, Costin Raiu, reports that the ransomware has made the most impact in the Ukraine, with the Russian Federation coming in at second. Poland takes third place, followed by Italy and then Germany. The infection is obviously spreading actively, so this list may not be accurate for long. One hopes it will not morph into a global outbreak.
UPDATE 5:45PM PST: As of this time, the network has hit the USA full force and is currently being covered on US news services. See the ABC news source for details.
The bitcoin wallet associated with this attack has already garnered more than 3.5 BTC at time of this writing, meaning at least some of the ransoms are being paid. The infection vector appears to be a compromised accounting software auto-update used common to most of the infected companies.
View at TechPowerUp Main Site
Last edited:



 .
.



