- Joined
- Oct 9, 2007
- Messages
- 47,293 (7.53/day)
- Location
- Hyderabad, India
| System Name | RBMK-1000 |
|---|---|
| Processor | AMD Ryzen 7 5700G |
| Motherboard | ASUS ROG Strix B450-E Gaming |
| Cooling | DeepCool Gammax L240 V2 |
| Memory | 2x 8GB G.Skill Sniper X |
| Video Card(s) | Palit GeForce RTX 2080 SUPER GameRock |
| Storage | Western Digital Black NVMe 512GB |
| Display(s) | BenQ 1440p 60 Hz 27-inch |
| Case | Corsair Carbide 100R |
| Audio Device(s) | ASUS SupremeFX S1220A |
| Power Supply | Cooler Master MWE Gold 650W |
| Mouse | ASUS ROG Strix Impact |
| Keyboard | Gamdias Hermes E2 |
| Software | Windows 11 Pro |
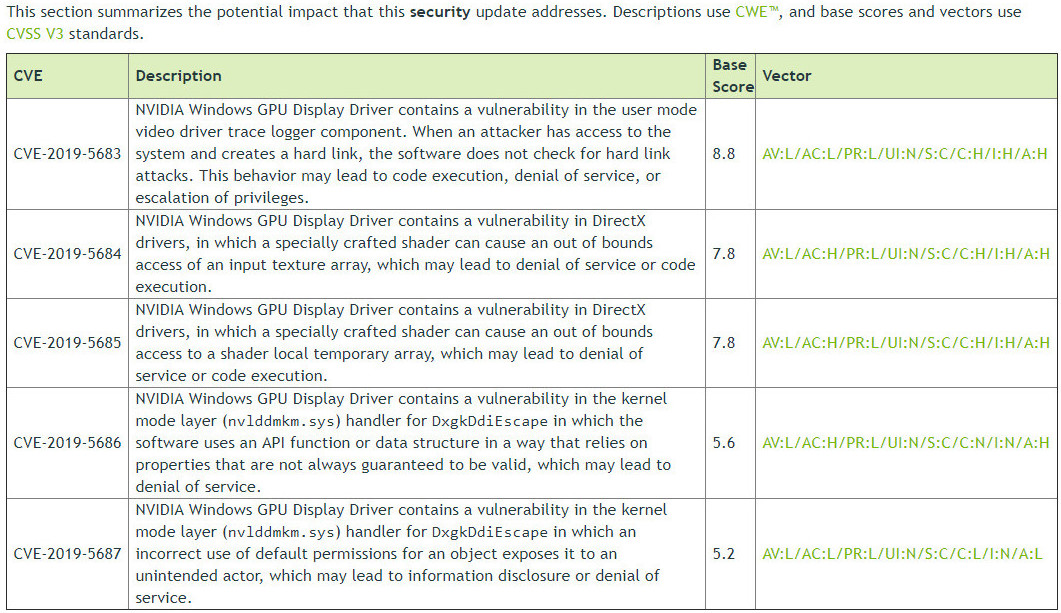
If you haven't updated your AMD Radeon drivers in a while, here's one major reason to. The company secretly patched four major security vulnerabilities affecting Radeon GPUs, in its recent Adrenalin 20.1.1 drivers, with no mention of doing so in its changelog. Talos Intelligence reports four vulnerabilities, which are are chronicled under CVE-2019-5124, CVE-2019-5146, CVE-2019-5147 and CVE-2019-5183. This class of attacks exploits a vulnerability in the AMD Radeon driver file ATIDXX64.dll, which can lead to denial of service or even remote code execution. What makes things much more serious is that this attack vector can be used to exploit the host machine from a VM (tested with VMWare). It even seems possible to trigger the vulnerability from a web page, through WebGL (which allows running 3D applications on a remote website). The vulnerabilities were tested on Radeon RX 550 / 550 Series VMware Workstation 15 (15.5.0 build-14665864) with Windows 10 x64 as guest VM, but there is no reason to assume that the issue is limited to just RX 550 as the AMD shader compiler shares a common code basis for all recent DirectX 12 GPUs.
All vulnerabilities rely on a common attack vector: specially crafted shader code that exploits bugs in the shader compiler. Even though HLSL shader code looks similar to assembly, it actually is a relatively high-level language that gets optimized and compiled by the graphics driver. VMWare's graphics acceleration lets you run 3D graphics in virtual machines, by passing along rendering info to the host GPU and then funneling the output back into the VM. Since the shader code gets compiled using the graphics driver of the host OS, this creates interesting opportunities for attacks.

Normally you'd expect the shader compiler to properly check all code it compiles and simply reject things that aren't supposed to work.
The last vulnerability is more serious, because it potentially allows remote code execution. If you pass a properly crafted shader, you can execute vTable methods, which give you control over code flow, instead of crashing with an error. With further bug exploitation that would let you execute arbitrary code that you supply.
All four vulnerabilities have been patched with Adrenalin 20.1.1 drivers. AMD rival NVIDIA also battles security vulnerabilities in secret, but the company tends to be more transparent in mentioning vulnerabilities patched in its driver release-notes. AMD's release notes for 20.1.1, in contrast omit any mention of the vulnerabilities, so most people aren't even aware that they should update their drivers to fix a security issue.
View at TechPowerUp Main Site
All vulnerabilities rely on a common attack vector: specially crafted shader code that exploits bugs in the shader compiler. Even though HLSL shader code looks similar to assembly, it actually is a relatively high-level language that gets optimized and compiled by the graphics driver. VMWare's graphics acceleration lets you run 3D graphics in virtual machines, by passing along rendering info to the host GPU and then funneling the output back into the VM. Since the shader code gets compiled using the graphics driver of the host OS, this creates interesting opportunities for attacks.

Normally you'd expect the shader compiler to properly check all code it compiles and simply reject things that aren't supposed to work.
- The first vulnerability, CVE-2019-5146, is briefly described as "AMD ATI Radeon ATIDXX64.DLL MAD shader functionality denial-of-service vulnerability."
- CVE-2019-5147 describes "AMD ATI Radeon ATIDXX64.DLL MOVC shader functionality denial-of-service vulnerability."
- CVE-2019-5124 points to "AMD ATI Radeon ATIDXX64.DLL shader functionality constant buffer denial-of-service vulnerability."
- CVE-2019-5183 talks about "AMD ATI Radeon ATIDXX64.DLL shader functionality VTABLE remote code execution vulnerability."
The last vulnerability is more serious, because it potentially allows remote code execution. If you pass a properly crafted shader, you can execute vTable methods, which give you control over code flow, instead of crashing with an error. With further bug exploitation that would let you execute arbitrary code that you supply.
All four vulnerabilities have been patched with Adrenalin 20.1.1 drivers. AMD rival NVIDIA also battles security vulnerabilities in secret, but the company tends to be more transparent in mentioning vulnerabilities patched in its driver release-notes. AMD's release notes for 20.1.1, in contrast omit any mention of the vulnerabilities, so most people aren't even aware that they should update their drivers to fix a security issue.
View at TechPowerUp Main Site