- Joined
- Oct 9, 2007
- Messages
- 47,293 (7.53/day)
- Location
- Hyderabad, India
| System Name | RBMK-1000 |
|---|---|
| Processor | AMD Ryzen 7 5700G |
| Motherboard | ASUS ROG Strix B450-E Gaming |
| Cooling | DeepCool Gammax L240 V2 |
| Memory | 2x 8GB G.Skill Sniper X |
| Video Card(s) | Palit GeForce RTX 2080 SUPER GameRock |
| Storage | Western Digital Black NVMe 512GB |
| Display(s) | BenQ 1440p 60 Hz 27-inch |
| Case | Corsair Carbide 100R |
| Audio Device(s) | ASUS SupremeFX S1220A |
| Power Supply | Cooler Master MWE Gold 650W |
| Mouse | ASUS ROG Strix Impact |
| Keyboard | Gamdias Hermes E2 |
| Software | Windows 11 Pro |
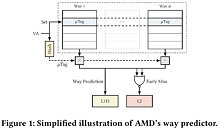
Cybersecurity researcher Moritz Lipp and his colleagues from the Graz University of Technology and the University of Rennes uncovered two new security vulnerabilities affecting all AMD CPU microarchitectures going back to 2011, detailed in a research paper titled "Take A Way." These include "Bulldozer" and its derivatives ("Piledriver," "Excavator," etc.,) and the newer "Zen," "Zen+," and "Zen 2" microarchitectures. The vulnerabilities are specific to AMD's proprietary L1D cache way predictor component. It is described in the security paper's abstract as a means for the processor to "predict in which cache way a certain address is located, so that consequently only that way is accessed, reducing the processor's power consumption."
By reverse engineering the L1D cache way predictor in AMD microarchitectures dating from 2011 to 2019, Lipp, et al, discovered two new attack vectors with which an attacker can monitor the victim's memory accesses. These vectors are named "Collide+Probe," and "Load+Reload." The paper describes the first vector as follows: "With Collide+Probe, an attacker can monitor a victim's memory accesses without knowledge of physical addresses or shared memory when time-sharing a logical core." The second vector is described as "With Load+Reload, we exploit the way predictor to obtain highly-accurate memory-access traces of victims on the same physical core." The two vulnerabilities have not been assigned CVE entries at the time of this writing. The research paper, however, describes the L1D cache way predictor in AMD processors as being vulnerable to attacks that can reveal contents of memory or even keys to a vulnerable AES implementation. For now there is no mitigation to these attacks, but the company is reportedly working on firmware and driver updates. Access the research paper here.
View at TechPowerUp Main Site
By reverse engineering the L1D cache way predictor in AMD microarchitectures dating from 2011 to 2019, Lipp, et al, discovered two new attack vectors with which an attacker can monitor the victim's memory accesses. These vectors are named "Collide+Probe," and "Load+Reload." The paper describes the first vector as follows: "With Collide+Probe, an attacker can monitor a victim's memory accesses without knowledge of physical addresses or shared memory when time-sharing a logical core." The second vector is described as "With Load+Reload, we exploit the way predictor to obtain highly-accurate memory-access traces of victims on the same physical core." The two vulnerabilities have not been assigned CVE entries at the time of this writing. The research paper, however, describes the L1D cache way predictor in AMD processors as being vulnerable to attacks that can reveal contents of memory or even keys to a vulnerable AES implementation. For now there is no mitigation to these attacks, but the company is reportedly working on firmware and driver updates. Access the research paper here.

View at TechPowerUp Main Site





