Synology DiskStation Manager Infected with a CryptoLocker Hack
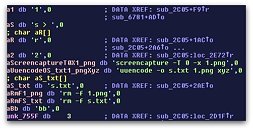
Synology DiskStation Manager (DSM), the company's in-house NAS operating system, is vulnerable to a CryptoLocker hack, which the company is referring to as "SynoLocker." The nature of how NAS units get infected by this hack is unknown, but when it is, the malware encrypts portion of data stored on your NAS volumes, and holds it for ransom, for 0.6 BTC (US $350 as of now). It decrypts that data only upon payment of that money. There's no guarantee of your data being held for ransom again. The issue is currently localized to NAS units running non-updated versions of DSM 4.3, but Synology is investigating if the hack works on DSM 5.0 as well.
Synology is urging users to take the following steps - close all ports for external (Internet) access, and unplug your NAS from your local network; and with your NAS plugged into just one machine, update DSM to the latest version; and back-up your data. If your NAS unit is infected, disconnect it from the network, perform a hard-shutdown, and contact Synology. The issue highlights one of the many dangers of a distributed currency, in which the beneficiary of funds is difficult to trace.
Here's an emergency statement from Synology (the company is preparing a press-release):
Synology is urging users to take the following steps - close all ports for external (Internet) access, and unplug your NAS from your local network; and with your NAS plugged into just one machine, update DSM to the latest version; and back-up your data. If your NAS unit is infected, disconnect it from the network, perform a hard-shutdown, and contact Synology. The issue highlights one of the many dangers of a distributed currency, in which the beneficiary of funds is difficult to trace.
Here's an emergency statement from Synology (the company is preparing a press-release):