Monday, January 29th 2018
It's a Web Mining Odyssey, Part 3: YouTube Falls to Injected Mining Code
Web mining's advent was the opening of a veritable Pandora's box when it comes to users' peace of mind while surfing the internet. What started with The Pirate Bay's implementation and ended up with a full-on browser war against these injected, unauthorized hijacks of users' electricity and computing resources has now taken to one of the world's most known and visited websites: YouTube.
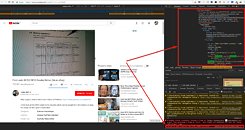
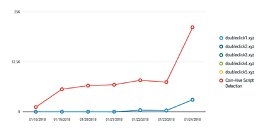
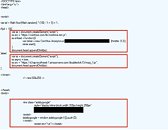
Users of YouTube started getting heads-up that something might be wrong due to their antivirus protection kicking off some cryptocurrency mining warnings that seemed to only pop up when users were visiting YouTube. These warnings kept popping up even after a web browser change, and then, on Friday, researchers from TrendMicro touched upon the issue, saying that YouTube's web mining injections had led to a more than three-fold spike in the total number of cryptocurrency web mining warnings. Luckily, the web mining exploit wasn't deployed across the entire world: Trend Micro researchers said that the attackers behind the ads were abusing Google's DoubleClick ad platform to display them to YouTube visitors in select countries, including Japan, France, Taiwan, Italy, and Spain.And this was a pretty aggressive miner as well, likely because its injectors knew it would be only a matter of time before their works were discovered (even so, TrendMicro says the miners went live on January 18th). The mining algorithm, which used publicly available Coinhive cryptomining code, hijacked 80% of users' CPU resources for the task - likely a way to reap as many reward as they could before their whole mining system was compromised. The attackers even went to the trouble of deploying a private web mining JavaScript code, so as to save themselves the 30% cut Coinhive takes for usage of its mining algorithms.In an e-mail sent to The Register, a Google representative wrote:
"Mining cryptocurrency through ads is a relatively new form of abuse that violates our policies and one that we've been monitoring actively. We enforce our policies through a multi-layered detection system across our platforms which we update as new threats emerge. In this case, the ads were blocked in less than two hours and the malicious actors were quickly removed from our platforms." Which apparently wasn't really the case, as trend Micro reported there where ads whose lifetime exceeded one week before being taken down.
Sources:
Trend Micro, Twitter user @ Mystic_Ervo, via Ars Technica, The Register
Users of YouTube started getting heads-up that something might be wrong due to their antivirus protection kicking off some cryptocurrency mining warnings that seemed to only pop up when users were visiting YouTube. These warnings kept popping up even after a web browser change, and then, on Friday, researchers from TrendMicro touched upon the issue, saying that YouTube's web mining injections had led to a more than three-fold spike in the total number of cryptocurrency web mining warnings. Luckily, the web mining exploit wasn't deployed across the entire world: Trend Micro researchers said that the attackers behind the ads were abusing Google's DoubleClick ad platform to display them to YouTube visitors in select countries, including Japan, France, Taiwan, Italy, and Spain.And this was a pretty aggressive miner as well, likely because its injectors knew it would be only a matter of time before their works were discovered (even so, TrendMicro says the miners went live on January 18th). The mining algorithm, which used publicly available Coinhive cryptomining code, hijacked 80% of users' CPU resources for the task - likely a way to reap as many reward as they could before their whole mining system was compromised. The attackers even went to the trouble of deploying a private web mining JavaScript code, so as to save themselves the 30% cut Coinhive takes for usage of its mining algorithms.In an e-mail sent to The Register, a Google representative wrote:
"Mining cryptocurrency through ads is a relatively new form of abuse that violates our policies and one that we've been monitoring actively. We enforce our policies through a multi-layered detection system across our platforms which we update as new threats emerge. In this case, the ads were blocked in less than two hours and the malicious actors were quickly removed from our platforms." Which apparently wasn't really the case, as trend Micro reported there where ads whose lifetime exceeded one week before being taken down.

24 Comments on It's a Web Mining Odyssey, Part 3: YouTube Falls to Injected Mining Code
The original Coinhive scripts license mandates an opt-out function. Sadly, these abusers don't give two shits about blatantly violating the TOS.
Me? I just want 50 bucks with no responsibility. And hell, it's just as unique as fucking garlicoin. I made $100 on that shit in two nights earlier.
EDIT; This is yet another reason why I block ads without exception.