Monday, February 12th 2018

Google To Integrate "Not Secure" Tag in Websites Sans HTTPS
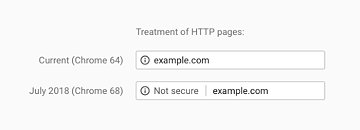
Google has been one of the more vocal advocates of a HTTPS-based web, and the company is mounting an offensive of sorts that aims to push web page managers to adopt the more secure protocol. Starting July of this year, with Chrome 68, the Google web browser will start marking all non-HTTPs websites as "Not secure", thus warning users of heightened security risks. From the way Google is doing this, it seems the company hopes users that see the "Not secure" badge on web pages will start gradually choosing other options for their web surfing habits - HTTPS-enabled options, ideally - and thus force page managers to upgrade their security to stem the leaving user base.
Google has some interesting bullet points as it pertains to the adoption of HTTPS; they say that over 68% of Chrome traffic on both Android and Windows is now protected; over 78% of Chrome traffic on both Chrome OS and Mac is now protected; and that 81 of the top 100 sites on the web use HTTPS by default (which this editor would personally expect to be closer to 100 out of 100, but there are just some websites that really can't be moved). In the blog post announcing the change, Google engineers also bring attention to the company's Lighthouse utility, which automagically scans web pages for non-HTTPS elements, highlighting them, and noting those that can easily and painlessly be converted to their secure, HTTPS equivalent - which in some cases, might even enable more powerful tools.
Source:
Chromium Blog
Google has some interesting bullet points as it pertains to the adoption of HTTPS; they say that over 68% of Chrome traffic on both Android and Windows is now protected; over 78% of Chrome traffic on both Chrome OS and Mac is now protected; and that 81 of the top 100 sites on the web use HTTPS by default (which this editor would personally expect to be closer to 100 out of 100, but there are just some websites that really can't be moved). In the blog post announcing the change, Google engineers also bring attention to the company's Lighthouse utility, which automagically scans web pages for non-HTTPS elements, highlighting them, and noting those that can easily and painlessly be converted to their secure, HTTPS equivalent - which in some cases, might even enable more powerful tools.
8 Comments on Google To Integrate "Not Secure" Tag in Websites Sans HTTPS