Friday, June 25th 2021

Western Digital: Disconnect WD My Book Live External HDDs From the Internet Immediately
Western Digital has issued a recommendation for all owners of the company's My Book Live and My Book Live Duo products - immediately disconnect them from the Internet or risk full data loss. The warning has come after reports started surfacing on distraught users of WD's My Book Live having their entire data deleted without any sort of user interaction or intervention. The recommendation will stay until the company can investigate and solve the issue that has led to the deletion of terabytes of data around the world.
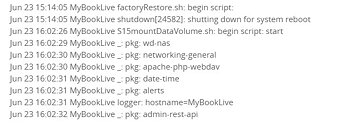
Apparently, factory resets were undertaken on the drives without any sort of user interaction. Some users have shared logs on what exactly happened. Western Digital stopped supporting their My Book Live products back in 2015, which means there are now six full years of operation (at the least) without any security updates. WD seems to believe that individual user accounts were compromised, and the company issued a statement regarding the ongoing investigation. If you have one of these products, take heed, and disconnect them from your network.
Sources:
via Ars Technica, Western Digital, TechPowerUp Forums
Apparently, factory resets were undertaken on the drives without any sort of user interaction. Some users have shared logs on what exactly happened. Western Digital stopped supporting their My Book Live products back in 2015, which means there are now six full years of operation (at the least) without any security updates. WD seems to believe that individual user accounts were compromised, and the company issued a statement regarding the ongoing investigation. If you have one of these products, take heed, and disconnect them from your network.


37 Comments on Western Digital: Disconnect WD My Book Live External HDDs From the Internet Immediately
I feel bad for that effort wasted on downloaded porn saved on them drives... :D :roll:
Mine is now 8 years old but thankfully Synology still provides updates until now.
Basically another tale of how important it is to not have stuff needlessly connected to the Internet. The affected drives were discontinued in 2014, and the bug above was found in 2018.
There are tools available like this one:
www.ccleaner.com/recuva#main-content
It happened ones to me that I accidentally chose wrong drive for quick format while wanted to install fresh copy of Windows onto my computer.
I was able to recover the whole data by using such a tool.
I feel sorry for those who have lost their data. Hope they have some sort of regular offline backups. For those who still want to use these products as a standard NAS, they will have to create some routing rules on their routers to cut off WAN access from/to these WD boxes.
But I guess it's time to salvage the drives in this PoS and use them in a safer, significantly better performing, classical fashion...Iirc, the encryption is done transparently on the hardware level, factory reset doesn't affect these keys, afaik. I think the problem here would be that recovery software can't get direct filesystem access. Though I do agree that the encryption would become a problem when attempting to directly connect the internal drive through a SATA connection).
Tricky situation but I would say its on the user to have their data in more than one place, but its also on WD to keep up on security updates if thats the expectation of the product.
That is, most hacks and breaches are successful because the IT security people in these organizations already knew of the vulnerability, had the necessary patch or fix (often for months!), but - due to shear laziness and lack of proper guidance from negligent upper management, they sat on their thumbs and neglected to install the patch or apply the fix.
If nothing else, as mentioned above, this should be yet another warning/reminder to everyone that we must all have "multiple" backups of any and all data we don't want to lose - and preferably with one copy maintained "off-site".
None of the internet attached devices will have a unlimited lifetime, hardware and software flaws are always going to be found and only offline local copies are immune to security issues.
However, WD support for these products was really crap. They came out in late 2011/early 2012. WD seems to have discontinued them by the end of 2012. Then they completely dropped support and stopped updating them in 2015. That is only 3 or maybe 4 years of support. That is pathetic for a web connected device that stores people's data. I'd expect 10 years of security updates at least. Maybe not feature updates, but at least security updates.You gotta realize the people that buy these tend to be tech ignorant. I mean, how many people out there are running routers with significantly outdated firmware? Even the ones with an web-update function sit with outdated firmware because people never log into the interface and actually tell it to apply the update.
I guess there would be some very nervous people wondering what happened to their data.
It does appear, however, that many users were able to recover their data with standard data recovery software, like Recuva. But of course, they should already have a backup copy of it anyway.
BTW, for those wondering, it would seem that the drive of subject in the above aritcle used the Universal Plug & Play protocol. Such a service should NEVER be allowed to run, regardless of the reason or need. It is a SwissCheese type security problem waiting to be exploited.