Intel's STORM Presents SAPM Paper on Hardware-Based Protection Against Side-Channel Execution Flaws
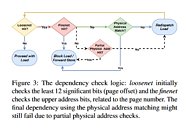
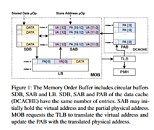
Intel's STrategic Offensive Research & Mitigations (STORM) department, which the company set up back in 2017 when it learned of side-channel attack vulnerabilities in its CPUs, have penned a paper detailing a proposed solution to the problem. Intel's offensive security research team counts with around 60 workers who focus on proactive security testing and in-depth investigations. Of that group, STORM is a subset of around 12 individuals who specifically work on prototyping exploits to show their practical impact. The solution proposed by this group is essentially a new memory-based hardware fix, going by the name of SAPM (Speculative-Access Protected Memory). The new solution would implement a resistant hardware fix in the CPU's memory that essentially includes blocks for known speculative-access hacks, such as the ones that hit Intel CPUs hard such as Meltdown, Foreshadow, MDS, SpectreRSB and Spoiler.
For now, the proposed solution is only at a "theory and possible implementation options" level. It will take a long time for it to find its way inside working Intel CPUs - if it ever does, really, since for now, it's just a speculative solution. A multitude of tests have to be done in order for its implementation to be approved and finally etched into good old silicon. Intel's STORM says that the SAPM approach would carry a performance hit; however, the group also calculates it to be "potentially lesser" than the current impact of all released software mitigations. Since the solution doesn't address every discovered side-channel attack specifically, but addresses the type of back-end operations that concern these attacks, the team is confident this solution would harden Intel CPUs against (most of) both known and not-yet-known speculative execution hacks.
For now, the proposed solution is only at a "theory and possible implementation options" level. It will take a long time for it to find its way inside working Intel CPUs - if it ever does, really, since for now, it's just a speculative solution. A multitude of tests have to be done in order for its implementation to be approved and finally etched into good old silicon. Intel's STORM says that the SAPM approach would carry a performance hit; however, the group also calculates it to be "potentially lesser" than the current impact of all released software mitigations. Since the solution doesn't address every discovered side-channel attack specifically, but addresses the type of back-end operations that concern these attacks, the team is confident this solution would harden Intel CPUs against (most of) both known and not-yet-known speculative execution hacks.