Tuesday, March 5th 2019

Spoiler Alert: New Security Vulnerability Found Affecting Intel CPUs
A new security vulnerability has been found that only affects Intel CPUs - AMD users need not concern regarding this issue. Dubbed Spoiler, the newfound security vulnerability was discovered by the Worcester Polytechnic Institute in partnership with the University of Lübeck, and affects all Intel CPUs since the introduction of their Core architecture. This vulnerability too affects Intel's speculative execution design, and according to the researchers, works independent of OS, virtual machine, or sandboxed environments.
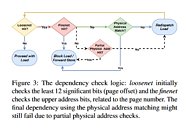
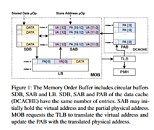
As the researchers explain, Intel's speculative execution of certain memory workloads requires the full physical address bits for the information in memory to be known, which could allow for the full address to be available in user space - allowing for privilege escalation and other microarchitectural attacks. According to the researchers, a software solution to this problem is impossible, which means this is yet another silicon-level bug that needs to be addressed in future processor designs.
Source:
White Paper
As the researchers explain, Intel's speculative execution of certain memory workloads requires the full physical address bits for the information in memory to be known, which could allow for the full address to be available in user space - allowing for privilege escalation and other microarchitectural attacks. According to the researchers, a software solution to this problem is impossible, which means this is yet another silicon-level bug that needs to be addressed in future processor designs.
114 Comments on Spoiler Alert: New Security Vulnerability Found Affecting Intel CPUs
"scare ware tactic" to sell more over priced CPU's...
If it ain't broke don't fix...well guess what? its broke again; "now we have to upgrade 1000's of our severs again""We just bought them last quarter!!"....lol...
This is most likely not accurate what I just wrote, but I can believe in market manipulation on almost any level....this would just be an extreme case of that.
I'm sure then, the next post will be "Why would Intel call foul on their own product? Because people will buy from them anyways because they are Intel....
Ever heard the phrase "All press is good press" its almost free advertisement in a way; though one might think it would hurt sales. The opposite effect
is most of the time observed....lol...that was my next thought....hahahhah
funney; and really kind of scary, but most likely true.
en.wikipedia.org/wiki/Intel_Management_Engine
...except my laptop and all of my other computers have Intel chips :banghead:
Only thing left with an Intel processor in the house is mum's old Toshiba P750 laptop with a i5 2410M from 2011. I'm waiting for it to die so I can get her a Raven Ridge machine like my Envy x360, Super happy with it, especially now the drivers from the main stack can be used on the 2500U.
I'm not worried about S/M or this but I'm starting to get a bad feel for Intel again.
And after I grab that sensitive data and figure out how to use it, I will clean my house with a toothpick.
On the other hand I suppose if consumers are okay with IME then we should be okay with another vulnerability. Thank you for reporting this.
Spectre based vulnerabilities do have software mitigations which come @ a performance cost. @ least that's better than Spoiler which, supposedly, can't be mitigated by software:
These attacks are important for datacenters, bank or government computers, etc.
If you have an Intel CPU, this doesn't mean that it is broken and you will be robbed if you still use it....
Also, discoveries like these give students and faculties some good press. Hey look, this is the place where that funky vulnerability was found. I see they got a habit of searching for bugs in CPUs, which is a good thing, sure, but CPUs are so complex machines that it is almost impossible to make them without some vulnerabilities. And don't worry, happy Ryzen users, AMD also has vulnerabilities, but they weren't discovered yet because nobody cares. Researches look at the market leader...
Nah, Intel would never..................:shadedshu: