Tuesday, March 5th 2019

Spoiler Alert: New Security Vulnerability Found Affecting Intel CPUs
A new security vulnerability has been found that only affects Intel CPUs - AMD users need not concern regarding this issue. Dubbed Spoiler, the newfound security vulnerability was discovered by the Worcester Polytechnic Institute in partnership with the University of Lübeck, and affects all Intel CPUs since the introduction of their Core architecture. This vulnerability too affects Intel's speculative execution design, and according to the researchers, works independent of OS, virtual machine, or sandboxed environments.
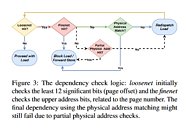
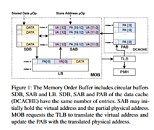
As the researchers explain, Intel's speculative execution of certain memory workloads requires the full physical address bits for the information in memory to be known, which could allow for the full address to be available in user space - allowing for privilege escalation and other microarchitectural attacks. According to the researchers, a software solution to this problem is impossible, which means this is yet another silicon-level bug that needs to be addressed in future processor designs.
Source:
White Paper
As the researchers explain, Intel's speculative execution of certain memory workloads requires the full physical address bits for the information in memory to be known, which could allow for the full address to be available in user space - allowing for privilege escalation and other microarchitectural attacks. According to the researchers, a software solution to this problem is impossible, which means this is yet another silicon-level bug that needs to be addressed in future processor designs.
114 Comments on Spoiler Alert: New Security Vulnerability Found Affecting Intel CPUs
Now, this has the potential to get real bad, relatively quickly and not just for servers once the hacking tools become more common and readily available.
They just didn't found the AMD one yet.
It's funny that a similar comment above got down voted.
Basically in principal (until systematically proven, but by the looks of it, sure seems likely) the exploit can run at the same time as a simple web site java script.
ie: The exploit can lift the information from server memory operations when lets say... it could be comparing passwords in memory for authorization and feed it back to the running java script which could just use it in a brute force attack, without needing the brute force anymore.
Do this fast enough even 2FA could be exploited.
The possibilities are wide open at this point. The more I'm reading, the more this seems like the most flexible exploit I've seen in a very long time.
forums.tomshardware.com/threads/my-corsair-h60-exploded.326466/
h ttps://www.reddit.com/r/buildapc/comments/4pxjp2/corsair_h100i_v2_exploded_on_my_3_day_old_build/
But if if some one asks whether this or that vulnerability from AMD / Intel presents a risk ... I have yet to come up with any real world scenario where someone says "this happened to me"
Neither 'side' should gloat. Any CPU that performs speculative execution is flawed.
Beyond that, it's of limited scope.It's all about making the data harder to get than it is worth.
That barrier works. Things like this massively break down that barrier, though.Begun, the clone wars has...
/yoda speak
It's like one of the oldest arguments for using Linux, or even Mac. "Everyone makes viruses for Windows! There are no viruses for Linux/Mac". Because Windows is by far the bigger target...
Why? One word. Root. Root is way too powerful.