Tuesday, March 5th 2019

Spoiler Alert: New Security Vulnerability Found Affecting Intel CPUs
A new security vulnerability has been found that only affects Intel CPUs - AMD users need not concern regarding this issue. Dubbed Spoiler, the newfound security vulnerability was discovered by the Worcester Polytechnic Institute in partnership with the University of Lübeck, and affects all Intel CPUs since the introduction of their Core architecture. This vulnerability too affects Intel's speculative execution design, and according to the researchers, works independent of OS, virtual machine, or sandboxed environments.
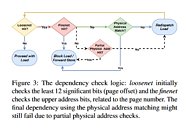
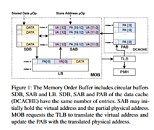
As the researchers explain, Intel's speculative execution of certain memory workloads requires the full physical address bits for the information in memory to be known, which could allow for the full address to be available in user space - allowing for privilege escalation and other microarchitectural attacks. According to the researchers, a software solution to this problem is impossible, which means this is yet another silicon-level bug that needs to be addressed in future processor designs.
Source:
White Paper
As the researchers explain, Intel's speculative execution of certain memory workloads requires the full physical address bits for the information in memory to be known, which could allow for the full address to be available in user space - allowing for privilege escalation and other microarchitectural attacks. According to the researchers, a software solution to this problem is impossible, which means this is yet another silicon-level bug that needs to be addressed in future processor designs.
114 Comments on Spoiler Alert: New Security Vulnerability Found Affecting Intel CPUs
This is something like checking parity of a file instead of its SHA to see if it's valid (a little exaggerated example, but that's the logic: let's cheat on any possible calculations).
@R-T-B 'Administrator' of Windows OS is the equivalent of SU in Linux.
So yes, the more exact equivalent of root would be the system account in Windows, of which privileges you can assimilate and use if you want.
Now we know how Intel chips seem to score well in Benchmarks LOLAMD nor ARM are affected by this.Good news for AMD, Bad news for Intel :D
Not only Intel but AMD, ARM and every other CPU manufacturer out there should take steps to get rid of spec - ex from their CPUs.
I agree that spec - ex is a "key feature" in current CPU's performance but if indeed it turns out that it's performance enhancement comes with too big security risks, than i'd rather have the companies that are most susceptible to be the target of these kinds of exploits (banks, and the like) to have slower CPUs.
Us individuals are much less prone to be the target of such attacks, but this fact doesn't rule it out: keep that in mind.
Other vulnerabilities may appear on all, but not this one.
The issue here is Intel cheating, where they finally got caught with there pants down.
New spec - ex based exploits are being discovered and, for all we know, other exploits just as dangerous or even more so may have been reported to manufacturers already. Remember: this new Spoiler exploit was referred to Intel in December of 2018, but we only found out about it in March 2019.I'm 100% sure that was the case. However, and if it turns out someone @ design level stages pointed out the potential issues that could arise from it but was ignored in the persuit of performance, then that's a different matter entirely. I'm not talking about Intel only, since AMD and ARM also use spec - ex.
I would guesstimate Intel will have something new in 2023-2025. Based on how long AMDs ZEN took.