AMD Have a Refreshed Bug Bounty Program with Rewards Up to $30,000
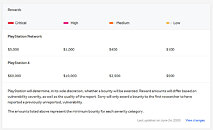
AMD has announced a new bug bounty program with prizes for individuals and public researchers. The company is partnering with the cloud security provider Intigriti on this new "bugs hunting campaign", this time, they have a better reward system with up to $30,000 in cash up for grab, while more people can take part. Bug bounties are not new in the industry, with modern hardware, bugs and issues have increased, this being a good way for companies to find vulnerabilities without spending too much on detection.
Individuals look for bugs, and then send a report to the company describing the bug and its impacts, AMD then gives prizes to the hunters based on factors like bug severity. It will be at least interesting to see what happens with AMD's new bug bounty program since public researchers can now take part.
(Eligible list with products and technologies below)
Individuals look for bugs, and then send a report to the company describing the bug and its impacts, AMD then gives prizes to the hunters based on factors like bug severity. It will be at least interesting to see what happens with AMD's new bug bounty program since public researchers can now take part.
(Eligible list with products and technologies below)