Friday, June 23rd 2017
WannaCry Strikes Again: Attack Forces Honda Factory to Shutdown
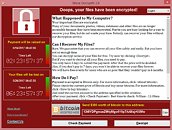
If you thought WannaCry was done, it would appear you were wrong. Honda has appeared as the latest victim of the outbreak, as late as this week. The outbreak was bad enough to stop production at its Sayama plant northeast of Tokyo. That factory can churn out nearly 1,000 vehicles a day, by the way, so this is not a small amount of money lost for the company.
The company says it discovered the malware Sunday, and by Wednesday it had managed to spread to several regions including Japan, North America, Europe, China and other locations (Sayama was the only place to experience an actual shutdown of operations, however).The outbreak was "solved" by this Tuesday, though there is no word on whether that solution involved paying the ransom or not. This is especially frustrating for Honda as their IT department had reportedly taken precautions against the worm only to be struck anyhow. The delivery method used for the WannaCry ransomware is unknown at this time, and one could theorize it may be a new variant, but that would be only theory at this point since there is unfortunately little technical information forthcoming in the source article.
Source:
Reuters.com
The company says it discovered the malware Sunday, and by Wednesday it had managed to spread to several regions including Japan, North America, Europe, China and other locations (Sayama was the only place to experience an actual shutdown of operations, however).The outbreak was "solved" by this Tuesday, though there is no word on whether that solution involved paying the ransom or not. This is especially frustrating for Honda as their IT department had reportedly taken precautions against the worm only to be struck anyhow. The delivery method used for the WannaCry ransomware is unknown at this time, and one could theorize it may be a new variant, but that would be only theory at this point since there is unfortunately little technical information forthcoming in the source article.
21 Comments on WannaCry Strikes Again: Attack Forces Honda Factory to Shutdown
virus did some good!
I guess that means he got caught and now can't collect.
So I don't feel bad for them at all.
trog
argue that its effects on Windows XP users were "insignificant" in comparison."
So, no. Xp is not the culprit here.