Wednesday, March 21st 2018

CTS-Labs Posts Ryzen Windows Credential Guard Bypass Proof-of-concept Video
CTS-Labs, following up on Tuesday's "Masterkey" exploit proof-of-concept video, posted a guide to bypassing Windows Credential Guard on an AMD Ryzen-powered machine. We once again begin in a privileged shell session, of an AMD-powered machine whose Secure Processor that has been compromised using admin privileges, by exploiting it using any of the 13 vulnerabilities chronicled by CTS-Labs. Mimikatz, a tool that is used by hackers to steal network credentials, should normally not work on a machine with Windows Credential Guard enabled. Using a modified version of Mimikatz, the CTS-Labs researchers are able to bypass Windows Credential Guard (which relies on hardware-level security features present on the processor), leveraging the AMD Secure Processor malware microcode they wrote.The proof-of-concept video follows.
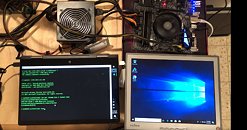
88 Comments on CTS-Labs Posts Ryzen Windows Credential Guard Bypass Proof-of-concept Video
bugto be called EPYCfail :rolleyes:C:\>bcdedit /copy {current} /d "No Hyper-V"
The entry was successfully copied to {your key}.
C:\>bcdedit /set {your key} hypervisorlaunchtype off
The operation completed successfully.
Definitely needed an AMD system for that.
It is obvious that CTS Labs will keep posting one video here, one video there because that's what they are getting payed to do, or because that's what they believe will keep their name on the news.
So, here is the question.
IS TPU going to become the main advertising platform for CTS Labs? And if yes, WHY?
Just update an older article. Is it so difficult? Or is it a great idea to make the security market the next online soap opera, so that tech sites can have plenty of drama to post?
Meanwhile I expect a lot of the comments here to be flagged as "low quality" :D
Dissecting the source and credibility of the source is extreme crucial in the age of massive data manipulation. End data consumers have every right to question the source and intent of the data before even diving into the content of the data.
First of All, if the attacker has ADMIN Access to your PC, he cand do anithing he wants, doenst matter if your use intel, Amd, Arm, VIA... but OK, Blame and focus only on AMD, fine. AMD with 24h of advance warning had to analise and give a statement about it (intel had months to analise and prepare before spectre and meltdown became public, but ok!) It becomes quite clear that CTS Labs had no intention of discovering flaws so those flaws can be fixed (helping make users more secure) it looks to me that they only wanted to deliver a blow to AMD to benefit from it, its a personal agenda. (my Opinion, Sorry my bad english)
This is what you can do when you have administrative access to a PC and BIOS. GG no matter which CPU you have.
As for further coverage of CTS labs technical pieces, it should be noted that the majority of TPU members (from what I've seen) are not that tech savvy. This is not my site (nor do I own one) but as Anandtech and others have done, a fair reflection on the merits of CTS background funding and PR roadshow wouldn't go amiss. There is one thing that will be proven in time and that is a very viable path for discrediting this exploit expose:
CTS says it's not fixable
CTS gives AMD 24 hours notice that they have found said exploit.
AMD says a firmware patch will fix it and they are working on it.
so.....
If patch fixes problem, and it does so within 90 days (standard industry timescale for exploit announcement)...
There would be no issue at all. This is the crux of it all - by not giving due time as is normally allowed, CTS have used unfair media leverage to make AMD look bad. If AMD do patch this (apparently unfixable issue) it makes CTS look like opportunistic little scum bags. This exploit would be history before it was even news but CTS intentionally released the exploit reveal with as little time as possible for AMD to make them look crap.
Therefore, all the PR the tech sites are allowing CTS 'airtime' is actually helping them look better when we're not giving AMD time to work on it as Google gave Intel (and AMD) when Spectre/Meltdown were discovered.
So, even those doing this :banghead: at those saying there is no flaw, of course there's a flaw but it could have been dealt with 'properly' and had it been done so (been fixed by AMD), we would not have had all this hyperbolic forum activity.
Is there an exploit? YES. Did CTS stitch AMD up? YES. TPU has not sufficiently asked why that is, that is why there is a great resentment in the forums.
Then again, in 'x' weeks time, if AMD hasn't fixed it, then we can get all pissy again.....
I am interested in news an appreciative of time and work put on this site (i appreciated nextpowerup too, a lot of news/info different from usual). I agreed to some reviews/editorials while i disagreed with other ones, anyways I personally see the risk for this website to burn itself. I know that depending on the stance you get accused of being pro or against the different "camps", however with this CTS vs AMD at moment you are not giving any service nor special info.
There is no added value in the last posts you are putting on the site, it has been cleared in a quite definitive way that you need "administrative" access to the machine to compromise it, and if the machine is behind a protected network you need to pierce the defenses, before.
I think everybody here has witnessed in the past years to several patches to different bugs in processors, chipsets and so on, from each "camp". Mostly often we discovered the bug or the glitch after the a solution was posted .
Now it seems really beating the dead horse, it does not give any help or additional info. If you keep posting news about this affair that add zero to what already written it will really give the idea that your are click-baiting, and this is good in the short term but on the long term it will heavily hurt.
While the vulnerabilities are real and have been confirmed as such, CTS-Labs is very much in question because of how they handed the disclosure, if not for other reasons as well. As such, it seems to me that it's a dis-service to "TPUers" to keep posting new topics about this when it could be covered in the original topic.
wccftech.com/report-alleges-amd-ryzen-epyc-cpus-suffer-13-fatal-security-flaws/
I held TPU to higher quality previously.