CTS-Labs Posts Ryzen Windows Credential Guard Bypass Proof-of-concept Video
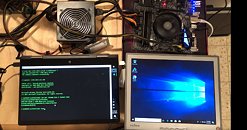
CTS-Labs, following up on Tuesday's "Masterkey" exploit proof-of-concept video, posted a guide to bypassing Windows Credential Guard on an AMD Ryzen-powered machine. We once again begin in a privileged shell session, of an AMD-powered machine whose Secure Processor that has been compromised using admin privileges, by exploiting it using any of the 13 vulnerabilities chronicled by CTS-Labs. Mimikatz, a tool that is used by hackers to steal network credentials, should normally not work on a machine with Windows Credential Guard enabled. Using a modified version of Mimikatz, the CTS-Labs researchers are able to bypass Windows Credential Guard (which relies on hardware-level security features present on the processor), leveraging the AMD Secure Processor malware microcode they wrote.The proof-of-concept video follows.