Wednesday, March 21st 2018

CTS-Labs Posts Ryzen Windows Credential Guard Bypass Proof-of-concept Video
CTS-Labs, following up on Tuesday's "Masterkey" exploit proof-of-concept video, posted a guide to bypassing Windows Credential Guard on an AMD Ryzen-powered machine. We once again begin in a privileged shell session, of an AMD-powered machine whose Secure Processor that has been compromised using admin privileges, by exploiting it using any of the 13 vulnerabilities chronicled by CTS-Labs. Mimikatz, a tool that is used by hackers to steal network credentials, should normally not work on a machine with Windows Credential Guard enabled. Using a modified version of Mimikatz, the CTS-Labs researchers are able to bypass Windows Credential Guard (which relies on hardware-level security features present on the processor), leveraging the AMD Secure Processor malware microcode they wrote.The proof-of-concept video follows.
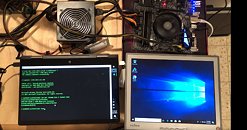
88 Comments on CTS-Labs Posts Ryzen Windows Credential Guard Bypass Proof-of-concept Video
How am I trolling, exactly?
Imagine you're just another desktop PC user running a Ryzen processor, and have the average joe's understanding of computers. You download a harmless looking free software (something that makes GIFs, converts videos, etc., to help you post dank memes). You run its installer, the installer seeks elevated privileges (in order to install software). You give it those privileges at the click of a button. That's it. You just gave something from the internet elevated privileges, enough to install a remote shell for a haxxor sitting across the globe, to access your hardware, and plant exploits that survive reboots and re-installs.They themselves admitted that they're a for-profit company that's paid by stock research firms (not Viceroy, but someone with an identical modus operandi).
(any users in my domain try something like this I'll just have a talk with them and point out the obvious, "you do not click on random stuff/files downloaded from the internet")
And yet again, we add a lot of "if" in order to make the CTS-Labs claims viable. Still no "staggering thirteen critical security vulnerabilities for AMD's "Zen" CPU microarchitecture" (quote from TPU original post).
blog.trailofbits.com/2018/03/15/amd-flaws-technical-summary/
I quote:
"There is no immediate risk of exploitation of these vulnerabilities for most users. Even if the full details were published today, attackers would need to invest significant development efforts to build attack tools that utilize these vulnerabilities. This level of effort is beyond the reach of most attackers (see www.usenix.org/system/files/1401_08-12_mickens.pdf, Figure 1)
These types of vulnerabilities should not surprise any security researchers; similar flaws have been found in other embedded systems that have attempted to implement security features. They are the result of simple programming flaws, unclear security boundaries, and insufficient security testing. In contrast, the recent Meltdown and Spectre flaws required previously unknown techniques and novel research advances to discover and exploit."
community.amd.com/community/amd-corporate/blog/2018/03/21/initial-amd-technical-assessment-of-cts-labs-research
I quote:
The security issues identified by the third-party researchers are not related to the AMD “Zen” CPU architecture or the Google Project Zero exploits made public Jan. 3, 2018. Instead, these issues are associated with the firmware managing the embedded security control processor in some of our products (AMD Secure Processor) and the chipset used in some socket AM4 and socket TR4 desktop platforms supporting AMD processors.
I find it weird to have continued discussion on this topic at the same original "staggering thirteen critical security vulnerabilities for AMD's "Zen" CPU microarchitecture " topic, since the magnitude of these issues was played as something they clearly werent. And this continues even after outside evaluation and AMDs reply. Somehow any bone CTS-Labs throws has so much weight to it..
For a fact, these exploits, based on POC, would be undeployable in environments i know of.
There are safeguards in place, for a reason.
I love it how CTS managed to make the installation of malware synonym to having a Ryzen processor.
Any new videos from CTS for the front page?
Can't say the same for ASMedia. Then again, no one seems to have addressed them specifically as all the focus is on AMD for some dumb reason...
the first video on Gamers Nexus about this makes a mention about that that EVERYONE ignored.
It's an interesting topic, to me. Like, this very clearly shows how AMD does things, and how they do business. In some ways they are an IP company, but they don't actually fully have enough of their own designs to provide a complete solution; they have to rely on other companies to complete things for them. It's kind of an "open-source" approach to hardware design, which can lead to all sorts of weird issues due to lack of communication between the separate teams at separate offices at separate companies...
AMD literally had ASMedia design their entire chipset.