Apr 2nd, 2025 10:53 EDT
change timezone
Latest GPU Drivers
New Forum Posts
- Upgrading...Video editing; CPU, GPU, SSD/NVMe , Memory; how important is each one? (8)
- compatibility for the I7 13620h (1)
- 5070 cards available below £550 in in the UK (6)
- TPU's Nostalgic Hardware Club (20153)
- Looking 4 a Solid AM5 MB? (3)
- Help me pick a UPS (25)
- New AM5 build [help] (4)
- OCCT power test shows a lot of error (0)
- Is RX 9070 VRAM temperature regular value or hotspot? (289)
- Weird things about 50 series. (1)
Popular Reviews
- DDR5 CUDIMM Explained & Benched - The New Memory Standard
- Sapphire Radeon RX 9070 XT Pulse Review
- SilverStone Lucid 04 Review
- ASRock Phantom Gaming B850 Riptide Wi-Fi Review - Amazing Price/Performance
- Palit GeForce RTX 5070 GamingPro OC Review
- Gigabyte GeForce RTX 5080 Gaming OC Review
- Sapphire Radeon RX 9070 XT Nitro+ Review - Beating NVIDIA
- Samsung 9100 Pro 2 TB Review - The Best Gen 5 SSD
- Assassin's Creed Shadows Performance Benchmark Review - 30 GPUs Compared
- be quiet! Pure Rock Pro 3 Black Review
Controversial News Posts
- MSI Doesn't Plan Radeon RX 9000 Series GPUs, Skips AMD RDNA 4 Generation Entirely (146)
- Microsoft Introduces Copilot for Gaming (124)
- AMD Radeon RX 9070 XT Reportedly Outperforms RTX 5080 Through Undervolting (119)
- NVIDIA Reportedly Prepares GeForce RTX 5060 and RTX 5060 Ti Unveil Tomorrow (115)
- Over 200,000 Sold Radeon RX 9070 and RX 9070 XT GPUs? AMD Says No Number was Given (100)
- NVIDIA GeForce RTX 5050, RTX 5060, and RTX 5060 Ti Specifications Leak (96)
- Retailers Anticipate Increased Radeon RX 9070 Series Prices, After Initial Shipments of "MSRP" Models (90)
- China Develops Domestic EUV Tool, ASML Monopoly in Trouble (88)
Monday, April 16th 2018
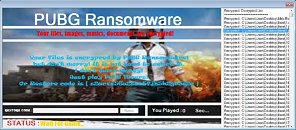
PUBG Ransomware Forces Users to Play PUBG to Decrypt Their Files
MalwareHunterTeam recently discovered the PUBG ransomware that is currently floating around the internet. When executed, the pesky program would encrypt the files and folders that are located on the victim's desktop and add the ".PUBG" extension to them. While meant to be more of a joke than actual malware, the program demands that the victim play PUBG for an hour. Nevertheless, users can decrypt their files in two ways. They can introduce the "s2acxx56a2sae5fjh5k2gb5s2e" code into the program and proceed to restore their files or launch the PUBG executable for three seconds. MalwareHunterTeam noted that the program runs a background check for a "TslGame" process, and therefore users can rename any executable to TslGame.exe and trick the malware into thinking that the fake executable is the real deal.
Source:
BleepingComputer
Apr 2nd, 2025 10:53 EDT
change timezone
Latest GPU Drivers
New Forum Posts
- Upgrading...Video editing; CPU, GPU, SSD/NVMe , Memory; how important is each one? (8)
- compatibility for the I7 13620h (1)
- 5070 cards available below £550 in in the UK (6)
- TPU's Nostalgic Hardware Club (20153)
- Looking 4 a Solid AM5 MB? (3)
- Help me pick a UPS (25)
- New AM5 build [help] (4)
- OCCT power test shows a lot of error (0)
- Is RX 9070 VRAM temperature regular value or hotspot? (289)
- Weird things about 50 series. (1)
Popular Reviews
- DDR5 CUDIMM Explained & Benched - The New Memory Standard
- Sapphire Radeon RX 9070 XT Pulse Review
- SilverStone Lucid 04 Review
- ASRock Phantom Gaming B850 Riptide Wi-Fi Review - Amazing Price/Performance
- Palit GeForce RTX 5070 GamingPro OC Review
- Gigabyte GeForce RTX 5080 Gaming OC Review
- Sapphire Radeon RX 9070 XT Nitro+ Review - Beating NVIDIA
- Samsung 9100 Pro 2 TB Review - The Best Gen 5 SSD
- Assassin's Creed Shadows Performance Benchmark Review - 30 GPUs Compared
- be quiet! Pure Rock Pro 3 Black Review
Controversial News Posts
- MSI Doesn't Plan Radeon RX 9000 Series GPUs, Skips AMD RDNA 4 Generation Entirely (146)
- Microsoft Introduces Copilot for Gaming (124)
- AMD Radeon RX 9070 XT Reportedly Outperforms RTX 5080 Through Undervolting (119)
- NVIDIA Reportedly Prepares GeForce RTX 5060 and RTX 5060 Ti Unveil Tomorrow (115)
- Over 200,000 Sold Radeon RX 9070 and RX 9070 XT GPUs? AMD Says No Number was Given (100)
- NVIDIA GeForce RTX 5050, RTX 5060, and RTX 5060 Ti Specifications Leak (96)
- Retailers Anticipate Increased Radeon RX 9070 Series Prices, After Initial Shipments of "MSRP" Models (90)
- China Develops Domestic EUV Tool, ASML Monopoly in Trouble (88)
12 Comments on PUBG Ransomware Forces Users to Play PUBG to Decrypt Their Files
TPU Staff you can do better
RutinaDeCifrado seems like DecypheringRoutine
BusarArchivos seems like ShearchArchives
Didn't bother to change his default class name Form1 to something meaningful though ... and he detects process only by name (edit: ah, it's what article is about)
"Want to play a cruel joke on your buddies? Send them a copy of the PUBG ransomware."
I don't think it's a good idea to give people ideas, either. There's nothing humorous about this malware.