Bitcoin's Lack of Wallet Privacy Leads Criminals to Look Towards Other Cryptos
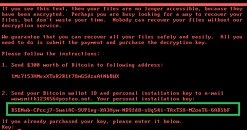
"It is used for criminal, illegal activities" is one of the most oft-mentioned reasons for users to reject Bitcoin or other cryptocurrencies. However, it seems that this argument is losing weight as we speak when it comes to Bitcoin. In the wake of much increased interest and awareness regarding the fledgling, currently leading cryptocurrency, which has seen institutions and states renew their interest and attention towards regulation or stricter control of the virtual currency, users that would use Bitcoin for nefarious purposes have started to migrate to other cryptocurrencies. You see, the reality of a distributed, transparent ledger is great for a system's transparency; however, transparency and easily identifiable - and traceable - wallets and transactions go against criminals' interests. Law enforcement agencies, such as Europol, have already issued warnings and established protocols towards the adoption of software tools to monitor people using bitcoin. As such, criminals are looking towards other less "transparent" cryptos to use as escape routes for their criminal ways.
The most viable alternative for criminals has apparently been Monero, the cryptocurrency that has also been in the world's mouth because it's usually the one being mined in web browsers, absent of users' consent. Monero has been developed with privacy as a main design criteria from the start, encrypting the recipient's address on its blockchain and generating fake addresses, obfuscating the real sender, but going one step further by also obfuscating the amount of the transaction. This means Monero is currently "one of the favorites, if not the favorite" for usage in ransomware attacks, said Matt Suiche, founder of Dubai-based security firm Comae Technologies, said in a phone interview to Bloomberg.
The most viable alternative for criminals has apparently been Monero, the cryptocurrency that has also been in the world's mouth because it's usually the one being mined in web browsers, absent of users' consent. Monero has been developed with privacy as a main design criteria from the start, encrypting the recipient's address on its blockchain and generating fake addresses, obfuscating the real sender, but going one step further by also obfuscating the amount of the transaction. This means Monero is currently "one of the favorites, if not the favorite" for usage in ransomware attacks, said Matt Suiche, founder of Dubai-based security firm Comae Technologies, said in a phone interview to Bloomberg.