Friday, June 30th 2017
Petya/NotPetya: The Ransomware That Wasn't Actually Looking to Ransom Anything
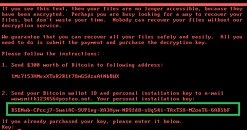
You've heard of the Petya ransomware by now. The surge, which hit around 64 countries by June 27th, infected an estimated 12,500 computers in Ukraine alone, hitting several critical infrastructures in the country (just goes to show how vulnerable our connected systems are, really.) The number one hit country was indeed Ukraine, but the wave expanded to the Russian Federation, Poland, and eventually hit the USA (the joys of globalization, uh?) But now, some interesting details on the purported ransomware attack have come to light, which shed some mystery over the entire endeavor. Could it be that Petya (which is actually being referred to as NotPetya/SortaPetya/Petna as well, for your reference, since it mostly masquerades as that well-known ransomware) wasn't really a ransomware attack?Let's get this clear: there was a ransomware edge to this attack, of that there is no doubt. Petya worked as most ransomwares do: encrypting a given computer's files and NTFS libraries, forcing devices to reboot, and then displaying ransom demands, with instructions detailing how to pay for the liberation of the encrypted files. However, the way in which this was done is unusual, to say the least. There are a number of ways to go about demanding ransoms; wallet addresses for cryptocurrency are the most common. What is strange in this whole affair is that the would-be perpetrators of the attack used a public email address (provided by Posteo) for their ransom demands. Naturally, Posteo closed down the e-mail account as soon as it became clear their service was being used for nefarious purposes (whether or not this was the best course of action is debatable.) But this closed the sole means of communication between the perpetrators and their victims, which now had no way to contact them towards obtaining the wallet address where they were supposed to send funds, nor receiving eventual decryption keys. Now I don't know about you, but a group capable of forking a variant of a GoldenEye ransomware and leading it to infect thousands of computers and critical infrastructure didn't consider this might happen? I don't buy it.
An information security researcher that goes by the pseudonymous "the grugq" had this to say regarding Petya/NotPetya:
"Although the worm is camouflaged to look like the infamous Petya ransomware, it has an extremely poor payment pipeline. There is a single hardcoded BTC wallet and the instructions require sending an email with a large amount of complex strings (something that a novice computer victim is unlikely to get right.) If this well engineered and highly crafted worm was meant to generate revenue, this payment pipeline was possibly the worst of all options (short of "send a personal cheque to: Petya Payments, PO Box …"). The superficial resemblance to Petya is only skin deep. Although there is significant code sharing, the real Petya was a criminal enterprise for making money. This is definitely not designed to make money. This is designed to spread fast and cause damage, with a plausibly deniable cover of "ransomware."
So, basically coders competent enough for such a fork chose the worst possible payment channel available, despite numerous cases of actual ransomware "done right", if you'll allow me. Kaspersky labs went on with an update, where Anton Ivanov and Orkhan Mamedov confirmed that the attackers "cannot decrypt victims' disk, even if a payment was made." They go on saying that "This supports the theory that this malware campaign was not designed as a ransomware attack for financial gain. Instead, it appears it was designed as a wiper pretending to be ransomware. (...)
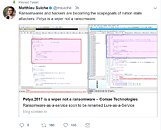
Another analyst from Comae Technologies came to the same conclusion regarding the attack, saying that "Ransomware and hackers are becoming the scapegoats of nation state attackers. Petya is a wiper, not a ransomware."
The fact that this particular version of the Petya ransomware had its patient zero in the Me-doc software, which is one of only two approved accounting software in Ukraine and the most widely used in Ukrainian companies and government, means that "an attack launched from MeDoc would hit not only Ukraine's government but many foreign investors and companies." The Me-doc infection vector was later confirmed by the Ukrainian police's cyber-security department.It seems this ransomware attack was nothing more than a wiper attack, disguised as ransomware, with the sole purpose of infecting as much of Ukraine's infrastructure and essential services as possible, while attempting infection of businesses connected with the country (which is likely why the infection spread through those at least 64 countries we mentioned at the beginning of this piece.)
It would appear a vaccine of sorts was in the meantime found towards thwarting this version of Petya, preventing it from running its installation algorithm on your computer (perhaps a fail-safe from the perpetrators so as to avoid their own machines from being infected with the malware?) Researchers from Serper advanced (and this was later confirmed by other independent security research agencies) that Petya looks for a particular file on systems, aborting its installation if it finds said file. To make yourself immune to the Petya installation, according to the researchers (and I have to put a little disclaimer here that other versions of the software could perfectly change the target lookup file), you should "create a file called perfc in the C:\Windows folder and make it read only. A batch file is available, created by Bleeping Computer's owner Lawrence Abrams.
Sources:
Tom's Hardware, "the grugq" Medium, On the Wire, Kaspersky Labs, Comae Security, Bleeping Computer
An information security researcher that goes by the pseudonymous "the grugq" had this to say regarding Petya/NotPetya:
"Although the worm is camouflaged to look like the infamous Petya ransomware, it has an extremely poor payment pipeline. There is a single hardcoded BTC wallet and the instructions require sending an email with a large amount of complex strings (something that a novice computer victim is unlikely to get right.) If this well engineered and highly crafted worm was meant to generate revenue, this payment pipeline was possibly the worst of all options (short of "send a personal cheque to: Petya Payments, PO Box …"). The superficial resemblance to Petya is only skin deep. Although there is significant code sharing, the real Petya was a criminal enterprise for making money. This is definitely not designed to make money. This is designed to spread fast and cause damage, with a plausibly deniable cover of "ransomware."
So, basically coders competent enough for such a fork chose the worst possible payment channel available, despite numerous cases of actual ransomware "done right", if you'll allow me. Kaspersky labs went on with an update, where Anton Ivanov and Orkhan Mamedov confirmed that the attackers "cannot decrypt victims' disk, even if a payment was made." They go on saying that "This supports the theory that this malware campaign was not designed as a ransomware attack for financial gain. Instead, it appears it was designed as a wiper pretending to be ransomware. (...)
Another analyst from Comae Technologies came to the same conclusion regarding the attack, saying that "Ransomware and hackers are becoming the scapegoats of nation state attackers. Petya is a wiper, not a ransomware."
The fact that this particular version of the Petya ransomware had its patient zero in the Me-doc software, which is one of only two approved accounting software in Ukraine and the most widely used in Ukrainian companies and government, means that "an attack launched from MeDoc would hit not only Ukraine's government but many foreign investors and companies." The Me-doc infection vector was later confirmed by the Ukrainian police's cyber-security department.It seems this ransomware attack was nothing more than a wiper attack, disguised as ransomware, with the sole purpose of infecting as much of Ukraine's infrastructure and essential services as possible, while attempting infection of businesses connected with the country (which is likely why the infection spread through those at least 64 countries we mentioned at the beginning of this piece.)
It would appear a vaccine of sorts was in the meantime found towards thwarting this version of Petya, preventing it from running its installation algorithm on your computer (perhaps a fail-safe from the perpetrators so as to avoid their own machines from being infected with the malware?) Researchers from Serper advanced (and this was later confirmed by other independent security research agencies) that Petya looks for a particular file on systems, aborting its installation if it finds said file. To make yourself immune to the Petya installation, according to the researchers (and I have to put a little disclaimer here that other versions of the software could perfectly change the target lookup file), you should "create a file called perfc in the C:\Windows folder and make it read only. A batch file is available, created by Bleeping Computer's owner Lawrence Abrams.

31 Comments on Petya/NotPetya: The Ransomware That Wasn't Actually Looking to Ransom Anything
Lol, Posteo can look forward to some lawsuits from companies who now have no way to decrypt their files, idiots >.>
Overall nothing will be done and no concesquences enforced.
You can have some tech doc writeups here, deduce the differences etc.
blog.malwarebytes.com/threat-analysis/2016/04/petya-ransomware/
blog.checkpoint.com/2016/04/11/decrypting-the-petya-ransomware/
as they say security in education.
Jesus journalism has gone in the shitter.
Education fixes this not settling. The bleeping computer article IIRC even states Kaspersky renamed it after finding out it wasnt related, leaving Petya in the name because people like this site were referencing it as such, but atleast THEY explain what it isn't.
Atleast people infected with actual Petya that might be able to save there systems will probably not reference sites like this for help.
It would be a shame to tell someone they have chickenpox when they have the plague.
I'm being a dick. No excuse, it may be a good idea to atleast include the other namesakes so that users may more easily differentiate from the original infection in 2016, as this is not necessarily the same infection.
The Bleeping Computer article also refers to it as Petya, though with the other different names referenced as well. Perhaps that was the cause of dissent between us.
I've updated the title's article and included a reference in the main body text that it is being called other names as well, so as to better inform the readers. I believe that was what you were trying to achieve?
Can't disagree with your metaphor though (I do love me some accurate metaphors).
Edit:
"Could it be that Petya (which is actually being referred to as NotPetya/SortaPetya/Petna as well, for your reference, since it mostly masquerades as that well-known ransomware) wasn't really a ransomware attack?"
Perhaps this helps readers. So thanks for pointing out the article's weakness :)
That said I only raised concern because this is what I do to pay bills. Petya as it was originally referenced was done because initial infections looked like it. However after disassembly it was found that only the dropper method was taken from petya the actual damage done (petya 2016 can be saved) and exploit methods were completely different. At that point they classed it as something different altogether but left petya because less experienced firms were already calling it such.
however I don’t like false hope and I just think it’s important to make the differentiation because people that have petya vs people that have notpetya are in very different boats
IMHO NotPetya isn't the work of a state actor or a hacker group. It screams lone amateur to me. Heck I could probably write a better payload than this.
1) Kaspersky lab published their findings on June 26th, while others like ESET, Avast, and Symantec were still arguing that this is indeed Petya. I would've totally missed the whole "virus" thing, if not for my pretty neighbor who couldn't access her online banking at 11:30PM the night before her birthday.
2)One correction: it is effectively the only one since the nationwide ban on 1C accounting software complex, along with Kaspersky AV, Dr.Web and some other "evil russian software and web-services".
M.E.Doc is pretty much forced for all tax filings and non-cash transaction accounting in my country. There are few other alternatives, but they are just as bad, if not worse than M.E.Doc.
BTW, M.E.Doc website is down since yesterday.
3) Everyone still calls it Petya, because of ignorant news outlets and a simple habit. Even in official announcements and press-releases from the Security Service of Ukraine it is still called Petya.A (maybe they do it on purpose to piss of those russians from Kaspersky Lab).
4) Also in yesterday's recommendation/announcement Cybersecurity dpt. said, that the primary source of the attack were fishing e-mails with "loaded" MS Word/PDF documents.
Exploiting M.E.Doc vulnerability was only the second stage of the attack.That was my impression since the start of the attack.