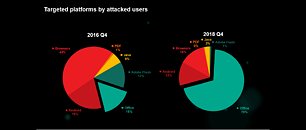
The Year is Still New at KeysWorlds, Bid Farewell to Windows 7 Saving Big
KeysWorlds began 2020 with a bang offering the lowest possible prices on genuine, globally-valid software your PC can't do without, such as genuine Windows 10, Office 2019 (and 2016), and leading PC security software from the likes of Kaspersky and Trend Micro. You'll be happy to know that KeysWorlds has extended its sale, and its introductory prices are still in effect! This would be a great time to upgrade your Windows 7 machine to Windows 10 Pro at just $9.95 with a TechPowerUp-exclusive discount; buy twin-packs of Windows 10 Pro for less than the sum of the whole; pick up Office 2019 Professional Plus for less than your annual Office 365 license, or benefit from Windows+Office bundles for new PC builders. KeysWorlds only sells genuine software licenses, and uses PayPal payment gateway to secure both your purchase and your payment instrument.
Apply the coupon-code KWNY35 on the items below to avail the prices you see here.
Buy Windows 10 Pro for $9.95 | Buy Windows 10 Home for $10.66 | Buy Windows 10 Pro Twin-Pack for $16.35 | Buy Office 2016 Professional Plus for $23.46 | Buy Office 2019 Professional Plus for $44.08 | Buy Windows 10 Pro + Office 2016 Professional Bundle for $27.73 | Buy Windows 10 Pro + Office 2019 Professional Bundle for $49.77
Apply the coupon KWNY25 on the following items for the prices you see here.
Buy Kaspersky Antivirus 1-PC 1-year for $19.69 | Buy Kaspersky Internet Security 1-PC 1-year for $21.32 | Buy McAfee Antivirus 1-PC 1-year for $13.12 | Buy McAfee Internet Security 1-PC 1-year for $14.67 | Buy Trend Micro Maximum Security 3-PC 1-year for $9.84
Apply the coupon-code KWNY35 on the items below to avail the prices you see here.
Buy Windows 10 Pro for $9.95 | Buy Windows 10 Home for $10.66 | Buy Windows 10 Pro Twin-Pack for $16.35 | Buy Office 2016 Professional Plus for $23.46 | Buy Office 2019 Professional Plus for $44.08 | Buy Windows 10 Pro + Office 2016 Professional Bundle for $27.73 | Buy Windows 10 Pro + Office 2019 Professional Bundle for $49.77
Apply the coupon KWNY25 on the following items for the prices you see here.
Buy Kaspersky Antivirus 1-PC 1-year for $19.69 | Buy Kaspersky Internet Security 1-PC 1-year for $21.32 | Buy McAfee Antivirus 1-PC 1-year for $13.12 | Buy McAfee Internet Security 1-PC 1-year for $14.67 | Buy Trend Micro Maximum Security 3-PC 1-year for $9.84