Tuesday, March 10th 2020

AMD Processors Since 2011 Hit with Cache Attack Vulnerabilities: Take A Way
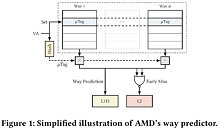
Cybersecurity researcher Moritz Lipp and his colleagues from the Graz University of Technology and the University of Rennes uncovered two new security vulnerabilities affecting all AMD CPU microarchitectures going back to 2011, detailed in a research paper titled "Take A Way." These include "Bulldozer" and its derivatives ("Piledriver," "Excavator," etc.,) and the newer "Zen," "Zen+," and "Zen 2" microarchitectures. The vulnerabilities are specific to AMD's proprietary L1D cache way predictor component. It is described in the security paper's abstract as a means for the processor to "predict in which cache way a certain address is located, so that consequently only that way is accessed, reducing the processor's power consumption."
By reverse engineering the L1D cache way predictor in AMD microarchitectures dating from 2011 to 2019, Lipp, et al, discovered two new attack vectors with which an attacker can monitor the victim's memory accesses. These vectors are named "Collide+Probe," and "Load+Reload." The paper describes the first vector as follows: "With Collide+Probe, an attacker can monitor a victim's memory accesses without knowledge of physical addresses or shared memory when time-sharing a logical core." The second vector is described as "With Load+Reload, we exploit the way predictor to obtain highly-accurate memory-access traces of victims on the same physical core." The two vulnerabilities have not been assigned CVE entries at the time of this writing. The research paper, however, describes the L1D cache way predictor in AMD processors as being vulnerable to attacks that can reveal contents of memory or even keys to a vulnerable AES implementation. For now there is no mitigation to these attacks, but the company is reportedly working on firmware and driver updates. Access the research paper here.
Source:
Cowcotland
By reverse engineering the L1D cache way predictor in AMD microarchitectures dating from 2011 to 2019, Lipp, et al, discovered two new attack vectors with which an attacker can monitor the victim's memory accesses. These vectors are named "Collide+Probe," and "Load+Reload." The paper describes the first vector as follows: "With Collide+Probe, an attacker can monitor a victim's memory accesses without knowledge of physical addresses or shared memory when time-sharing a logical core." The second vector is described as "With Load+Reload, we exploit the way predictor to obtain highly-accurate memory-access traces of victims on the same physical core." The two vulnerabilities have not been assigned CVE entries at the time of this writing. The research paper, however, describes the L1D cache way predictor in AMD processors as being vulnerable to attacks that can reveal contents of memory or even keys to a vulnerable AES implementation. For now there is no mitigation to these attacks, but the company is reportedly working on firmware and driver updates. Access the research paper here.
46 Comments on AMD Processors Since 2011 Hit with Cache Attack Vulnerabilities: Take A Way
What are the chances this is easily mitigated, and also, at this data level it seems it would slow the machine to a crawl to actually implement, and what about memory encryption, the processor doesn't know what the data being processed is.
Either way, I believe we are at a milestone here for both companies, where reverse engineering is going to reveal more issues of varying severity as they snipe at each other. At the end of the day we the consumer win with more secure products.
Funding research on security problems that affects your own CPU designs, as well as your competitors is one thing.
Funding research to reverse engineer your competitors CPU design to uncover potential security problems is another....this is my "issue" with this finding.
Kinda like your neighbor with bad gardening skills is hiring some blokes to go over to your front lawn to dig a fresh new a hole into it.
Then said blokes go in front of their freshly dug hole while pointing at it and be like: "Yo everybody this a**hole has a hole in his lawn!"
Then you be like with standing in your doorway with a coffee mug and crumpled news paper: "Well no sh*t, you just dug one..."
So in this new cache issue...
Is this a problem? It is now.
Should AMD do something about it? Also yes, if they can.No worries I'll crawl back to by cave as suggested.
Research into all kinds of undocumented functionalities is a constant effort. For example a link about finding undocumented opcodes was making rounds last week - www.cattius.com/images/undocumented-cpu-behavior.pdf. Edit: Now that I look at it, the presentation seems to originate from the same Graz TU.
2. TaW uses collisions in L1D way predictor. TaW is an another one side-channel, like cache-collisions and branch buffers, that can be used by other flaws, like Spectre V1&2
3. TaW can be used to weak ASLR
Intels contributions to the research may be innocent or there may be other motives, we'll never know exactly. Timing is everything.
www.tomshardware.com/news/new-amd-side-channel-attacks-discovered-impacts-zen-architecture
Author of that tweet is one of the authors of Take A Way paper, he is likely to know what he claims.
Please, hold on for my rand on the second clause, it is coming with more effervescence i must add.
I might be railing too hard. Lost my train of thought for a moment.
Let's look at it the other way - how easy would it be to cover latency imprint by masking with false accesses? It boggles my mind how much validation is accredited to indirect proofs.
I'm not such a cave troll, but we survived rowhammer, haven't we?