Report: PC Gaming On The Rise
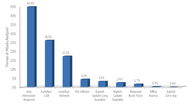
This may not be a surprise to the PC enthusiast community but, the PC gaming market has never been healthier, according to a report from the not-for-profit consortium PC Gaming Alliance (PCGA). The report claims that in 2011, the industry reached a global record $18.6 billion, a growth of 15 percent over the prior year. The report cites burgeoning foreign markets and social games as large factors in the findings. The results of the PCGA's third annual "Horizons" research report found that China is growing at almost twice the rate of the global market, bringing in $6 billion for a total growth of 27 percent. The US, UK, Korea, Japan, and Germany saw increased revenue of 11%, by comparison. Asian companies, in general, are noted for spurring on sales in their markets.
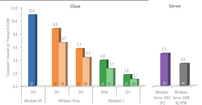
The report also cites Zynga and Nexon (of MapleStory fame) as frontrunners in the PC space. Zynga in particular doubled its revenue to roughly $1.1 billion, putting it on-par with Nexon. Zynga and the German company Bigpoint were noted for pushing the free-to-play model, already popular in Asian territories, into North America and Europe. The report also notes the movers and shakers of big-budget PC games from the western market, like Star Wars: The Old Republic and Rift, along with multiplatform titles like Battlefield 3 and Call of Duty: Modern Warfare 3. Looking forward, the report speculates that the industry will grow to $25.5 billion (37 percent increase) by 2015, thanks to increased broadband penetration and digital delivery. The report is from a PC gaming coalition with a vested interest in trumpeting the industry's health, but even so, the rumors of PC's death have greatly exaggerated.
The report also cites Zynga and Nexon (of MapleStory fame) as frontrunners in the PC space. Zynga in particular doubled its revenue to roughly $1.1 billion, putting it on-par with Nexon. Zynga and the German company Bigpoint were noted for pushing the free-to-play model, already popular in Asian territories, into North America and Europe. The report also notes the movers and shakers of big-budget PC games from the western market, like Star Wars: The Old Republic and Rift, along with multiplatform titles like Battlefield 3 and Call of Duty: Modern Warfare 3. Looking forward, the report speculates that the industry will grow to $25.5 billion (37 percent increase) by 2015, thanks to increased broadband penetration and digital delivery. The report is from a PC gaming coalition with a vested interest in trumpeting the industry's health, but even so, the rumors of PC's death have greatly exaggerated.