Thursday, April 23rd 2020

Security Researchers Turn Radeon GPU into a Radio Transmitter with 50ft Range to Steal Data
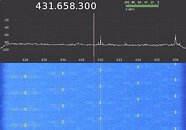
Thursday we brought you a story of an improbable but ingenious cybersecurity attack vector called Air-ViBER, which uses fan vibrations to transmit data to a nearby listening device in an air-gapped environment. Another team of researchers, led by Mikhail Davidov and Baron Oldenburg, developed an equally ingenious but more insidious attack vector - rapid manipulation of clock speeds of an AMD Radeon Pro WX3100 GPU to turn it into a tunable radio transmitter; and ferrying data off as inaudible and invisible RF transmissions. The graphics card itself works as a radio transmitter, the computer needn't have a WLAN device.
What's worse, the signal has an impressive 50-foot (15.2 m) range, can pass through walls, and can have a far higher data-rate than the fan vibration hack. Even worse, the attack doesn't require any special hacks of the GPU driver or physical modification of the graphics card in any way - only a tool that can manipulate its clock speeds (any overclocking software can do that). Luckily, overclocking tools are privileged applications (requiring ring-0 access), and in most machines it springs up a UAC gate unless the overclocking software installs a driver and service that runs in the background (this installation requires a UAC authorization in the first place). If someone managed to install privileged software on your computer, you have bigger problems than a graphics card that likes to sing. Find technical details of the hack here, and a video presentation here.
Sources:
Mikhail Davidov, via Tom's Hardware
What's worse, the signal has an impressive 50-foot (15.2 m) range, can pass through walls, and can have a far higher data-rate than the fan vibration hack. Even worse, the attack doesn't require any special hacks of the GPU driver or physical modification of the graphics card in any way - only a tool that can manipulate its clock speeds (any overclocking software can do that). Luckily, overclocking tools are privileged applications (requiring ring-0 access), and in most machines it springs up a UAC gate unless the overclocking software installs a driver and service that runs in the background (this installation requires a UAC authorization in the first place). If someone managed to install privileged software on your computer, you have bigger problems than a graphics card that likes to sing. Find technical details of the hack here, and a video presentation here.
19 Comments on Security Researchers Turn Radeon GPU into a Radio Transmitter with 50ft Range to Steal Data
It is present in MSI Afterburner for instance.
What 5G spying?Oh god, please no.Honestly, it's just as practical as half of this, and not a bad idea. You could even set it to target a specific small pixel to avoid user notice. Because James Bonds screen capture software is always pixel-perfect... ENHANCE!
I worked on the call desk for a defense contractor and one specific computer acted up. He had to write instructions down and error messages and hand carry them to said computer because his phone wouldn't work in the building because as he put it, it's inside a sheilded concrete area to protect it from any possible attack on the em spectrum or someone sneaking in wireless devices to capture data. I couldn't see this type of attack working.
What kind of data? This sounds more like script kiddie fun project rather than serious security problem.