Wednesday, October 12th 2016

AMD's ZEN to Implement Advanced Security Features not found in Intel's solutions
Thanks to AMD's incorporation of an ARM-based "AMD Secure Processor" in their upcoming ZEN micro-architecture, the company is poised to offer something competitor Intel's microprocessors yet don't: memory encryption. This processor, and its underlying technologies, could prove to be a stepping-stone for AMD towards regaining lost server market share. Essentially, because in a market ever more steered by cloud computing considerations, it allows for the client's data to be encrypted at every moment of the work chain. Assuming all works as intended, for the first time not even cloud providers, with either hypervisor-level privileges or even physical access to the servers, will be able to carry out any malicious actions against their clients.
One only has to consider the writing on the wall: Morgan Stanley predicts that by 2018, 30% of Microsoft's revenue will stem from its cloud services; Amazon Web Services (AWS) generated $7.88B in revenue on Q4 2015, up 69% over 2014; and worldwide spending on public cloud services by itself will grow from $70B in 2015 to an estimated $141B in 2019. Cloud computing is here to stay, and with security being as important as it is for some businesses, this is an important area of investment for AMD. This "AMD Secure Processor" will work on essentially two fronts: SME (Secure Memory Encryption) and SEV (Secure Encrypted Virtualization), backed by an hardware-based SHA (Secure Hash Algorithm).According to AMD's Memory Encryption Whitepaper, SME works by leveraging the Secure Processor in encrypting data (using a 128-bit AES encryption key) when it is written to DRAM, effectively putting an end to the last redoubt of Cleartext-stored data. This becomes increasingly important when one considers the advent of NVDIMM (non volatile memory), which if left unencrypted, would be much more vulnerable to physical removal and subsequent cloning of its contents than currently employed solutions. This encryption key is randomly generated by the Secure Processor on each system reset, and is never accessible by any software running on the CPU cores. Furthermore, AMD states that the encryption impact on performance (namely, latency on memory accesses) is, quote, "very small", even when the entirety of the addressable memory is encrypted, but especially considering the Security Processor's ability to encrypt only specific memory pages, and not the entire amount of used RAM.
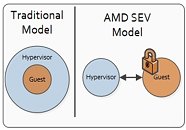
SEV, on the other hand, solves the problem with the traditional ring-based security system, where customer's code runs at a lower privilege level than the hypervisor. In essence, this means that in ring-based security, the hypervisor can have access to the guest's (ie., client's) data. With SEV, that will no longer be the case, isolating the hypervisor and the client's resources, as well as different client's workloads running on the same machine. Each of these workloads, as well as the hypervisor, will have their code and data tagged and separately encrypted, guaranteeing that each time the encrypted data is accessed by code with an incorrect encryption tag, all it sees is its encrypted state. SEV differs from SME in that in this case, the hypervisor must interact with the Secure Processor in order for the encryption to occur. It informs the Secure Processor that an encrypted VM (Virtual Machine) is going to run, and passes to the server's Secure Processor the needed certificates and exchange key which, in turn, allows the Secure Processor to load the appropriate, unique AES key.With the ever-expanding computing requirements of businesses and customers worldwide being increasingly serviced by servers on the so-called cloud, the need for increased security becomes more and more of a concern for service-providers. According to The 2016 Global Cloud Data Security Study, 60% of IT professionals consider it to be more difficult to protect confidential or sensitive information in the cloud. At the same time, it's estimated that globally, 36% of organization's total IT and data processing needs are met by cloud resources. This is expected to increase to 45% over the next two years.
And with 86% of the study's respondents claiming encryption will become even more important over the next two years, this feature disparity between AMD and Intel's solutions could prove to be an ace up AMD's sleeve in regaining some of its lost server market share from its glory days.
Sources:
2016 Global Cloud Data Security Study, AMD x86 Memory Encryption Technologies
One only has to consider the writing on the wall: Morgan Stanley predicts that by 2018, 30% of Microsoft's revenue will stem from its cloud services; Amazon Web Services (AWS) generated $7.88B in revenue on Q4 2015, up 69% over 2014; and worldwide spending on public cloud services by itself will grow from $70B in 2015 to an estimated $141B in 2019. Cloud computing is here to stay, and with security being as important as it is for some businesses, this is an important area of investment for AMD. This "AMD Secure Processor" will work on essentially two fronts: SME (Secure Memory Encryption) and SEV (Secure Encrypted Virtualization), backed by an hardware-based SHA (Secure Hash Algorithm).According to AMD's Memory Encryption Whitepaper, SME works by leveraging the Secure Processor in encrypting data (using a 128-bit AES encryption key) when it is written to DRAM, effectively putting an end to the last redoubt of Cleartext-stored data. This becomes increasingly important when one considers the advent of NVDIMM (non volatile memory), which if left unencrypted, would be much more vulnerable to physical removal and subsequent cloning of its contents than currently employed solutions. This encryption key is randomly generated by the Secure Processor on each system reset, and is never accessible by any software running on the CPU cores. Furthermore, AMD states that the encryption impact on performance (namely, latency on memory accesses) is, quote, "very small", even when the entirety of the addressable memory is encrypted, but especially considering the Security Processor's ability to encrypt only specific memory pages, and not the entire amount of used RAM.
SEV, on the other hand, solves the problem with the traditional ring-based security system, where customer's code runs at a lower privilege level than the hypervisor. In essence, this means that in ring-based security, the hypervisor can have access to the guest's (ie., client's) data. With SEV, that will no longer be the case, isolating the hypervisor and the client's resources, as well as different client's workloads running on the same machine. Each of these workloads, as well as the hypervisor, will have their code and data tagged and separately encrypted, guaranteeing that each time the encrypted data is accessed by code with an incorrect encryption tag, all it sees is its encrypted state. SEV differs from SME in that in this case, the hypervisor must interact with the Secure Processor in order for the encryption to occur. It informs the Secure Processor that an encrypted VM (Virtual Machine) is going to run, and passes to the server's Secure Processor the needed certificates and exchange key which, in turn, allows the Secure Processor to load the appropriate, unique AES key.With the ever-expanding computing requirements of businesses and customers worldwide being increasingly serviced by servers on the so-called cloud, the need for increased security becomes more and more of a concern for service-providers. According to The 2016 Global Cloud Data Security Study, 60% of IT professionals consider it to be more difficult to protect confidential or sensitive information in the cloud. At the same time, it's estimated that globally, 36% of organization's total IT and data processing needs are met by cloud resources. This is expected to increase to 45% over the next two years.
And with 86% of the study's respondents claiming encryption will become even more important over the next two years, this feature disparity between AMD and Intel's solutions could prove to be an ace up AMD's sleeve in regaining some of its lost server market share from its glory days.


31 Comments on AMD's ZEN to Implement Advanced Security Features not found in Intel's solutions
Currently proving myself to TPU's staff, so, here's my first news post. I hope you enjoy reading through it.
This could also be useful for laptops/2 in 1s. Perhaps OEMs will give AMD a fair shot here.
PS "im" "dont" "thouroughly"... :p
@Raevenlord
That's a really nice FIRST article. Don't worry, soon it will become easier and if you like news posting, an everyday habit.
The analysis can't be more concise, the English is (somewhat) better than most, non American, news sites and you should proof read your own posts
Regarding length, I tried to keep it as concise as possible, whilst going into as much detail as I considered relevant to you guys, without meandering into TL;DR territory (we've all been there, after all).Thanks, john_, I believe that's exactly the case.Ahh, I'm not sure that won't happen, but alas, your concern has been noted and well received :roll:That's exactly the target audience for this kind of technology, I'd wager. The everyday consumer might not think of it (though some tech-savvy users might want to make use of it), but for enterprises, I believe this is the natural and needed development. Ring-based security always needed that compromise of trusting the service provider. Now, not so much.
have one question related to news post:
i open news(with pictures) from front page and i can preview pictures and close them having the article in background
i open same news but from forum/news, if i watch one picture this is opened in a new page, forcing me to go back one page to view again the article , as i can't preview them...; isn't possible as above?
maybe is solvable but i'm not familiar with the script and can't help unfortunately.....
Congrats man. You seem to be an excellent news writer from this piece, and are well suited for this work if you can keep that grade up.
But as a news post it kinda fails, as this information has been known for well over a half a year now – ever since AMD pushed those patches to the linux kernel, implementing support for these features. xP
Either way, hope to see more of Your posts soon, as You really seem to have a knack for writing good, comprehensive and detailed articles.
Yahoo Reportedly Scanned All Emails On Behalf Of US Agencies | NextPowerUp
for a regular consumer this means:
- Makes cold boot attacks unviable. This is mostly a privacy concern as it can be and is used by authorities to recover encryption keys from a running system.
- Potentially makes DMA attacks useless. (i.e. does not protect against it, just makes it read garbage, i.e. useless)
- Potentially makes "ring -3" attacks useless. i.e. stuff like the gapping hardware backdoor in Intel ME would theoretically be useless, just like a DMA attack
(warning: I am by no means an expert, take whatever I wrote with a grain of salt)AMD Beema
That's not Zen so, either the picture is bull or Beema already has this feature and it's not new to Zen.