ETH Zurich Researchers Discover New Security Vulnerability in Intel Processors
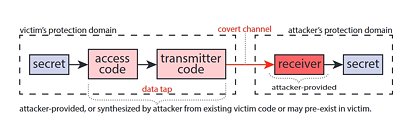
Computer scientists at ETH Zurich discover new class of vulnerabilities in Intel processors, allowing them to break down barriers between different users of a processor using carefully crafted instruction sequences. Entire processor memory can be read by employing quick, repeated attacks. Anyone who speculates on likely events ahead of time and prepares accordingly can react quicker to new developments. What practically every person does every day, consciously or unconsciously, is also used by modern computer processors to speed up the execution of programs. They have so-called speculative technologies which allow them to execute instructions on reserve that experience suggests are likely to come next. Anticipating individual computing steps accelerates the overall processing of information.
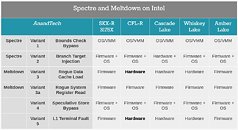
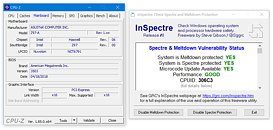
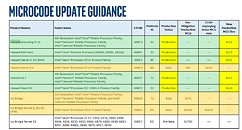
However, what boosts computer performance in normal operation can also open up a backdoor for hackers, as recent research by computer scientists from the Computer Security Group (COMSEC) at the Department of Information Technology and Electrical Engineering at ETH Zurich shows. The computer scientists have discovered a new class of vulnerabilities that can be exploited to misuse the prediction calculations of the CPU (central processing unit) in order to gain unauthorized access to information from other processor users.Update:: Intel released a security advisory regarding CVE-2024-45332, accompanied by a public announcement, and provided TechPowerUp with the following statement:
However, what boosts computer performance in normal operation can also open up a backdoor for hackers, as recent research by computer scientists from the Computer Security Group (COMSEC) at the Department of Information Technology and Electrical Engineering at ETH Zurich shows. The computer scientists have discovered a new class of vulnerabilities that can be exploited to misuse the prediction calculations of the CPU (central processing unit) in order to gain unauthorized access to information from other processor users.Update:: Intel released a security advisory regarding CVE-2024-45332, accompanied by a public announcement, and provided TechPowerUp with the following statement:
"We appreciate the work done by ETH Zurich on this research and collaboration on coordinated public disclosure. Intel is strengthening its Spectre v2 hardware mitigations and recommends customers contact their system manufacturer for the appropriate update. To date, Intel is not aware of any real-world exploits of transient execution vulnerabilities.", Intel spokesperson