Wednesday, February 28th 2018

Intel Finally Ready With Security Microcode Updates for Broadwell, Haswell
Via updated documents on its Microcode Revision guide, Intel has revealed that they have finally developed and started deploying microcode security updates for their Broadwell and Haswell-based microprocessors. The microcode update comes after a flurry of nearly platform-specific updates that aimed to mitigate known vulnerabilities in Intel's CPUs to the exploits known as Spectre and Meltdown.
While that's good news, Intel's patching odyssey still isn't over, by any means. According to Intel's documentation, the Spectre fixes for Sandy Bridge and Ivy Bridge are still in beta and are being tested by hardware partners, so that's two other architectures that still remain vulnerable. Of course, this discussion of who's vulnerable and isn't really can't be reduced to which architectures Intel has released its updates to. Users have to remember that the trickle-down process from Intel's patch validation and distribution through manufacturers to end users' systems is a morose one, and is also partially in the hands of sometimes not too tech-savy users. Time will tell if these flaws will have any major impact in some users or businesses.
Source:
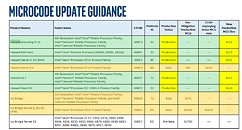
Intel Microcode Update Guidance
While that's good news, Intel's patching odyssey still isn't over, by any means. According to Intel's documentation, the Spectre fixes for Sandy Bridge and Ivy Bridge are still in beta and are being tested by hardware partners, so that's two other architectures that still remain vulnerable. Of course, this discussion of who's vulnerable and isn't really can't be reduced to which architectures Intel has released its updates to. Users have to remember that the trickle-down process from Intel's patch validation and distribution through manufacturers to end users' systems is a morose one, and is also partially in the hands of sometimes not too tech-savy users. Time will tell if these flaws will have any major impact in some users or businesses.



35 Comments on Intel Finally Ready With Security Microcode Updates for Broadwell, Haswell
Sandy Bridge?
I don't see it in the table. Oldest is see is Ivy Bridge and these appear to be mobile and Xeon variants only - not desktop LGA.
Saying that i'm suprised IB will even get the patch. I thought Haswell would be the oldest one to get it.
EDIT: Never mind. Looks like the linked PDF includes way more models. Some even...ancient like Peryn, Nehalem and Westmere (pre-Sandy Bridge).
This is why I miss Intel's Desktop Board brand. They were usually the first to receive new BIOSes and Intel would support them for way longer than someone like ASUS.
The Meltdown side will be green if the relevant MS security updates have been installed. The Spectre side will remain red until your motherboard's BIOS is updated to include Intel's latest CPU microcode patch.
they never get the first bios right.
Bios updates in general for me have become "do it only if broken, or if there is extra performance". I like to give them like 2-3 revisions before i update.