Intel GPUs Gain 20% Performance by Disabling Security Mitigations
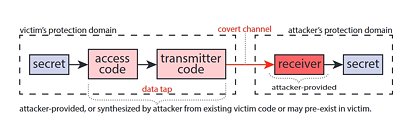
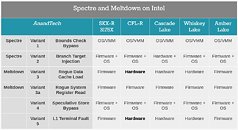
Intel GPUs, both iGPUs and Arc, on Linux, can achieve a surprising 20% performance boost by taking direct action within their own graphics stack. The company has long incorporated security mitigations into its open-source Compute Runtime to protect against vulnerabilities like Spectre, but these safeguards have carried a hidden cost. With the introduction of a build-time option named NEO_DISABLE_MITIGATIONS, Intel now allows users to compile the Compute Runtime without these extra checks, thereby reclaiming up to 20% in OpenCL and Level Zero workloads. Behind the scenes, Intel's engineers have been testing unmitigated builds on GitHub for months, and the results have been clear: disabling these driver-level mitigations can significantly speed up shader compilation, AI-driven upscaling routines, and physics simulations that rely on GPU compute.
Intel's confidence in disabling these checks stems from the fact that modern Linux kernels already address Spectre vulnerabilities comprehensively at the operating system level. To keep users informed, the Compute Runtime build will emit a warning if it detects a kernel lacking the necessary patches, ensuring transparency about any residual risk. Canonical's Ubuntu team has partnered with Intel to introduce this enhancement in its upcoming 25.10 release. But make no mistake, this is Intel's initiative: the company is driving the performance improvements, publishing unmitigated binaries upstream, and coordinating with distribution partners to make the change broadly available. Security teams at Intel have analyzed the potential attack surface and concluded that the performance gains far outweigh the minimal risk, especially given that Intel's own builds have been running unmitigated without incident.
Intel's confidence in disabling these checks stems from the fact that modern Linux kernels already address Spectre vulnerabilities comprehensively at the operating system level. To keep users informed, the Compute Runtime build will emit a warning if it detects a kernel lacking the necessary patches, ensuring transparency about any residual risk. Canonical's Ubuntu team has partnered with Intel to introduce this enhancement in its upcoming 25.10 release. But make no mistake, this is Intel's initiative: the company is driving the performance improvements, publishing unmitigated binaries upstream, and coordinating with distribution partners to make the change broadly available. Security teams at Intel have analyzed the potential attack surface and concluded that the performance gains far outweigh the minimal risk, especially given that Intel's own builds have been running unmitigated without incident.