Monday, January 8th 2018

NVIDIA GeForce 390.65 Driver with Spectre Fix Benchmarked in 21 Games
The Meltdown and Spectre vulnerabilities have been making many headlines lately. So far, security researchers have identified three variants. Variant 1 (CVE-2017-5753) and Variant 2 (CVE-2017-5715) are Spectre, while Variant 3 (CVE-2017-5754) is Meltdown. According to their security bulletin, NVIDIA has no reason to believe that their display driver is affected by Variant 3. In order to strengthen security against Variant 1 and 2, the company released their GeForce 390.65 driver earlier today, so NVIDIA graphics card owners can sleep better at night.
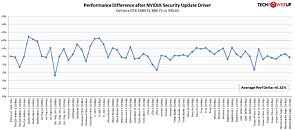
Experience tells us that some software patches come with performance hits, whether we like it or not. We were more than eager to find out if this was the case with NVIDIA's latest GeForce 390.65 driver. Therefore, we took to the task of benchmarking this revision against the previous GeForce 388.71 driver in 21 different games at the 1080p, 1440p, and 4K resolutions. We even threw in an Ethereum mining test for good measure. Our test system is powered by an Intel Core i7-8700K processor overclocked to 4.8 GHz, paired with G.Skill Trident-Z 3866 MHz 16 GB memory on an ASUS Maximus X Hero motherboard. We're running the latest BIOS, which includes fixes for Spectre, and Windows 10 64-bit with Fall Creators Update, fully updated, which includes the KB4056891 Meltdown Fix.We grouped all 21 games, each at three resolutions, into a single chart. Each entry on the X axis is for a single test, showing the percentage difference between old and new driver in percent. Negative values stand for a performance decrease when using today's driver. Positive numbers for performance gained.
Cryptominers can rest assured that the new GeForce 390.65 driver won't affect their profits negatively. Our testing shows zero impact in Ethereum mining. With regard to gaming, there is no significant difference in performance either. The new driver actually gains a little bit of performance on average over the previous version (+0.32%). The results hint at some undocumented small performance gains in Wolfenstein 2 and F1 2017; the other games are nearly unchanged. Even if we exclude those two titles, the performance difference is still +0.1%. The variations that you see in the chart above are due to random effects and due to limited precision on taking measurements in Windows. Generally, for the kind of testing done in our VGA reviews we typically expect 1-2% margin of error between benchmark runs, even when using the same game, at identical settings, on the same hardware.
Experience tells us that some software patches come with performance hits, whether we like it or not. We were more than eager to find out if this was the case with NVIDIA's latest GeForce 390.65 driver. Therefore, we took to the task of benchmarking this revision against the previous GeForce 388.71 driver in 21 different games at the 1080p, 1440p, and 4K resolutions. We even threw in an Ethereum mining test for good measure. Our test system is powered by an Intel Core i7-8700K processor overclocked to 4.8 GHz, paired with G.Skill Trident-Z 3866 MHz 16 GB memory on an ASUS Maximus X Hero motherboard. We're running the latest BIOS, which includes fixes for Spectre, and Windows 10 64-bit with Fall Creators Update, fully updated, which includes the KB4056891 Meltdown Fix.We grouped all 21 games, each at three resolutions, into a single chart. Each entry on the X axis is for a single test, showing the percentage difference between old and new driver in percent. Negative values stand for a performance decrease when using today's driver. Positive numbers for performance gained.
Cryptominers can rest assured that the new GeForce 390.65 driver won't affect their profits negatively. Our testing shows zero impact in Ethereum mining. With regard to gaming, there is no significant difference in performance either. The new driver actually gains a little bit of performance on average over the previous version (+0.32%). The results hint at some undocumented small performance gains in Wolfenstein 2 and F1 2017; the other games are nearly unchanged. Even if we exclude those two titles, the performance difference is still +0.1%. The variations that you see in the chart above are due to random effects and due to limited precision on taking measurements in Windows. Generally, for the kind of testing done in our VGA reviews we typically expect 1-2% margin of error between benchmark runs, even when using the same game, at identical settings, on the same hardware.
42 Comments on NVIDIA GeForce 390.65 Driver with Spectre Fix Benchmarked in 21 Games
BTW, Thank You for the links. Been doing a ton of research on these problems as they will directly affect my work, but those specific points I had not found/gotten to. I don't mind admitting that these developments leave me more than a little alarmed and deeply concerned.
EDIT: I'm also very glad that I keep many personal systems on a closed network that has no internet access.. Perhaps that might be a possible solution elsewhere.
GPUs are not affected. Driver does stuff on CPU that might be vulnerable to Spectre variants so mitigation measures are taken.
Mitigation measures introduce additional delays, that means performance hot for CPU-limited situations. So far, small hits, but still.
From the previous page of the topic:
Someone has a proper graph?
Note where the bigger performance hits occur - Divinity Original Sin 2 at 1080p, Dawn of War 3 at 1080p. These are the more CPU-heavy situations.
Yes, GTA5 at high resolutions does get hit more and more but I would suspect this is specific to that game, perhaps something about how assets or draw calls are distributed as that is a massive open world.
www.techspot.com/news/72691-nvidia-gpus-arent-immune-spectre-security-flaw.html
GPUs do not speculate.
Driver patches are taking care of the problem that might occur with drivers running stuff on CPU as with any other piece of software.